Free VMware 3V0-752 Exam Dumps
Here you can find all the free questions related with VMware Certified Advanced Professional 7 - Desktop Management Design Exam (3V0-752) exam. You can also find on this page links to recently updated premium files with which you can practice for actual VMware Certified Advanced Professional 7 - Desktop Management Design Exam . These premium versions are provided as 3V0-752 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the VMware Certified Advanced Professional 7 - Desktop Management Design Exam premium files for free, Good luck with your VMware Certified Advanced Professional 7 - Desktop Management Design Exam .MultipleChoice
The IT team for a company wants to deploy VMware Horizon and allow end users to access their Horizon Windows desktops using Windows laptops, Android and iOS mobile phones, and Android and iOS tablets with the following requirements:
High data security
Low client bandwidth
Low client processor overhead
Low storage space
High image quality
Which Horizon desktop pool meets these requirements?
OptionsMultipleChoice
A customer is looking to implement Horizon View Windows desktops for a 500-seat call center operating under these conditions:
Three 8-hout shifts
First and second shifts are 100% staffed
Third shift operates with reduced staffing of only 200 representatives
Management is frustrated by the lack of productivity that occurs during shift changeover. Logoff and logon processes take in excess of 5 minutes.
The customer has asked an architect to recommend the most cost-effective configuration that provides the shortest possible amount of downtime between shifts.
Which two should the architect choose? (Choose two.)
OptionsMultipleChoice
A company is proposing:
All external network users will access their desktop using BLAST protocol. No other protocol will be used.
Device will NOT be allowed to be attached to PCs while users are outside of the internal network.
VMware Unified Access Gateways will be deployed behind a secure network and strict security requirements implemented.
A consultant was brought in to determine backend firewall port requirements to support the proposal.
What are the minimum required firewall rules between the Unified Access Gateway appliance and back end components?
OptionsMultipleChoice
An architect is asked to analyze poor performance on a Horizon VDI environment and provide recommendations on how to improve the user experience.
The architect documents:
An ESXi cluster of 4 nodes using vSAN
Each node has 128GB of RAM, four 500GB 10K HDD, one 200GB SSD
Each desktop is configured with 4GB of RAM and 2vCPUs
Each desktop has a working set of 20 GB
The environment peaks at 150 concurrent desktops in use
What action can the architect recommend?
OptionsMultipleChoice
When meeting with a customer, these VM template requirements for instant-clone are determined:
2 vCPU
4 GB Memory
20 GB OS disk
Which is the formula to design a 40% utilization strategy for 80 desktops, given the above requirements?
OptionsMultipleChoice
An application packaging team is preparing to deploy a new enterprise application for 1000 users.
Application requirements and limitations include:
Windows 2012 R2 or Windows 10 64-bit OS
Installation of a PDF printer
Application only allows a single instance to be launched
1 GB RAM
The organization is only using Horizon hosted applications on Windows 2012 R2. The servers are at 30% utilization. No additional users will be added.
What changes to the Horizon environment will be required to deploy the application?
OptionsMultipleChoice
An architect has been asked to evaluate the existing Active Directory infrastructure to implement a Horizon 7-based virtual Desktop infrastructure.
The Active Directory Admin helped the architect create the attached exhibit related to the current Active Directory.
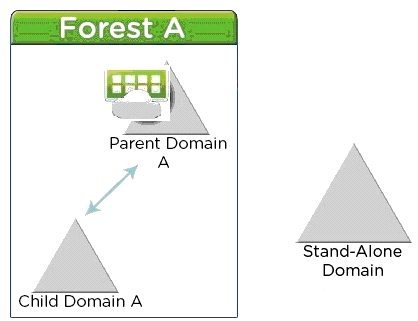
The customer specified these requirements:
Extend the same Horizon 7 infrastructure to a 20 User Organization from Stand-Alone Domain.
Two users from the Stand-Alone Domain must have Administration access to Horizon View Infrastructure.
The architect has been asked to recommend Active Directory changes with a constraint of least possible trust relationship and credential duplication to meet the additional requirement.
Referring to the exhibit, which two recommendations would enable Active Directory infrastructure to meet requirements?
OptionsMultipleChoice
A customer wants to securely deliver applications. They have given these requirements to an architect:
1,100 corporate users
Applications run on Windows
Confidential data must remain inside the datacenter at all times
Datacenter has a firewall separating it off from the corporate LAN
Security team policy will NOT allow a corporate LAN subnet through the firewall to a datacenter subnet (example: source 172.16.30.0 /24, destination 10.10.1.0 /24 would NOT be allowed)
Security team policy does allow corporate LAN subnets to access specific datacenter IP addresses (example: source 172.16.30.0 /24, destination 10.10.1.100 /24 would be allowed)
50 of the 1,100 internal users work exclusively on tablets, some Android and some IOS devices
Which two recommendations can the architect propose? (Choose two.)
Options
