Free Palo Alto Networks PCNSE Exam Dumps
Here you can find all the free questions related with Palo Alto Networks Certified Security Engineer PAN-OS 11.0 (PCNSE) exam. You can also find on this page links to recently updated premium files with which you can practice for actual Palo Alto Networks Certified Security Engineer PAN-OS 11.0 Exam. These premium versions are provided as PCNSE exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the Palo Alto Networks Certified Security Engineer PAN-OS 11.0 Exam premium files for free, Good luck with your Palo Alto Networks Certified Security Engineer PAN-OS 11.0 Exam.DragDrop
Match the terms to their corresponding definitions

















MultipleChoice
Refer to the diagram. Users at an internal system want to ssh to the SSH server The server is configured to respond only to the ssh requests coming from IP 172.16.16.1.
In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?

MultipleChoice
An organization conducts research on the benefits of leveraging the Web Proxy feature of PAN-OS 11.0.
What are two benefits of using an explicit proxy method versus a transparent proxy method? (Choose two.)
. No client configuration is required for explicit proxy, which simplifies the deployment complexity.
OptionsDragDrop
Match the terms to their corresponding definitions

















MultipleChoice
A network administrator wants to use a certificate for the SSL/TLS Service Profile.
Which type of certificate should the administrator use?
OptionsMultipleChoice
Using multiple templates in a stack to manage many firewalls provides which two advantages? (Choose two.)
OptionsMultipleChoice
An administrator wants to enable WildFire inline machine learning. Which three file types does WildFire inline ML analyze? (Choose three.)
OptionsMultipleChoice
What are three types of Decryption Policy rules? (Choose three.)
OptionsDragDrop
Place the steps in the WildFire process workflow in their correct order.
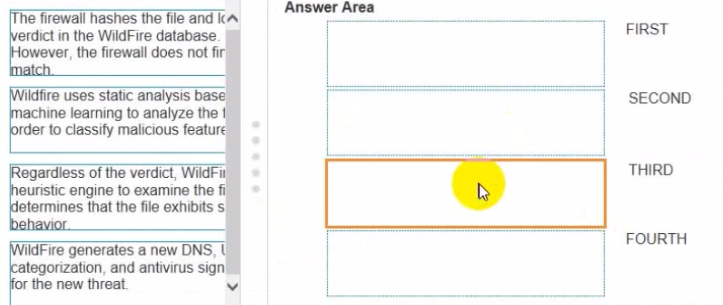
















MultipleChoice
Review the images. A firewall policy that permits web traffic includes the
What is the result of traffic that matches the 'Alert - Threats' Profile Match List?
Options
