Free Palo Alto Networks PCNSA Exam Dumps
Here you can find all the free questions related with Palo Alto Networks Certified Network Security Administrator (PCNSA) exam. You can also find on this page links to recently updated premium files with which you can practice for actual Palo Alto Networks Certified Network Security Administrator Exam. These premium versions are provided as PCNSA exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the Palo Alto Networks Certified Network Security Administrator Exam premium files for free, Good luck with your Palo Alto Networks Certified Network Security Administrator Exam.MultipleChoice
Which type of profile must be applied to the Security policy rule to protect against buffer overflows illegal code execution and other attempts to exploit system flaws''
OptionsDragDrop
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.
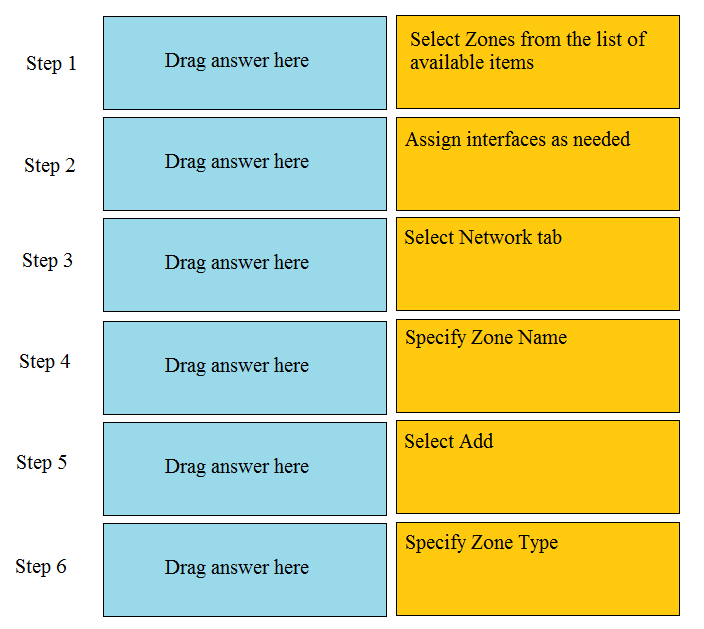
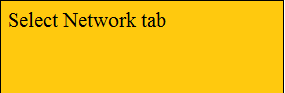


































Step 1 -- Select network tab
Step 2 -- Select zones from the list of available items
Step 3 -- Select Add
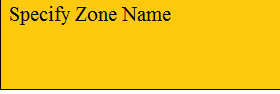
Step 4 -- Specify Zone Name
Step 5 -- Specify Zone Type
Step 6 -- Assign interfaces as needed
MultipleChoice
Which option shows the attributes that are selectable when setting up application filters?
OptionsMultipleChoice
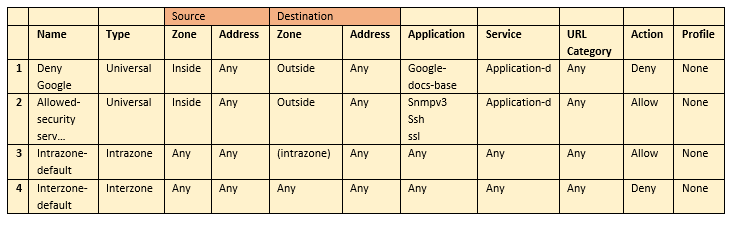
Employees are shown an application block page when they try to access YouTube. Which security policy is blocking the YouTube application?
MultipleChoice
Complete the statement. A security profile can block or allow traffic.
OptionsMultipleChoice
In the example security policy shown, which two websites would be blocked? (Choose two.)
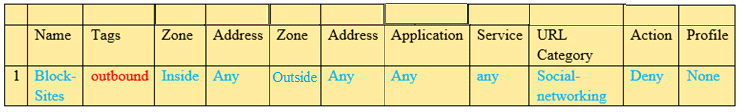
MultipleChoice
Which path in PAN-OS 9.0 displays the list of port-based security policy rules?
OptionsMultipleChoice
Exhibit:
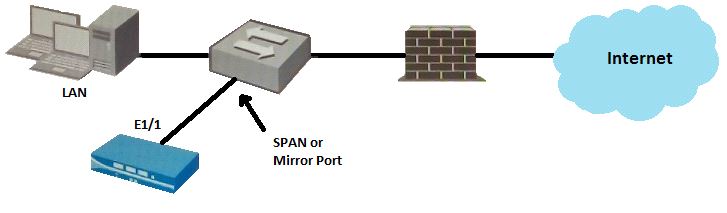
Given the topology, which zone type should interface E1/1 be configured with?
OptionsMultipleChoice
In a security policy what I the quickest way to rest all policy rule hit counters to zero?
Options
