Deal of The Day! Hurry Up, Grab the Special Discount - Save 25% - Ends In 00:00:00 Coupon code: SAVE25
Palo Alto Networks PCCSA Exam Questions
Status: RETIRED
Exam Name: Palo Alto Networks Certified Cybersecurity Associate
Exam Code:
PCCSA
Related Certification(s): Palo Alto Networks Certified Cybersecurity Associate Certification
Certification Provider: Palo Alto Networks
Number of PCCSA practice questions in our database:
79
(updated: 03-06-2021)
Expected PCCSA Exam Topics, as suggested by Palo Alto Networks :
- Topic 1: Modern Computing Trends/ New Application Framework And Threat Vectors
- Topic 2: Recent High-Profile Cyber-Attack Examples/ Attackers And Movivations/ Modern Cyber-Attack Strategy
- Topic 3: Cyber-Attack Techniques And Types/ Vulnerabilities And Exploits/ Advance Persistent Threats
- Topic 4: Introduction To Networking Devices/ Routed And Routing Protocols/ Area Networks And Topologies
- Topic 5: Packet Encapulation And Licecycle/ Perimeter-Based Network Security Strategy/ Cloud And Data Center Security
- Topic 6: Cloud Computing Security Considerations And Requirements/ Traditional Data Security Solution Weaknesses
- Topic 7: Implementing Security Technologies/ Instrusion Detection And Prevention Systems/ Virtual Private Networks/ Data Loss Prevention
- Topic 8: Security Information And Event Management/ Host-Based Instrustion Prevention Systems (HIPS)
- Topic 9: Cloud, Virtualization, And Storage Security/ Server And System Administration
- Topic 10: Structured Host And Network Troubleshooting/ Help Desk And Technical Support/ Security Operationg Platform
- Topic 11: Palo Alto Networks Expedition (Migration Tool)/ Network Security Management (Panorama)/ Mobile Secruity And VPN Management
- Topic 12: Cloud Monitoring And Compliance (Evident)/ Behavioral Analytics (Magnifier)/ Log Management (Logging Service)/ Threat Intelligence (Autofocus) Optimizing Firewall Threat Prevention/ Managing Firewalls At Scale
Disscuss Palo Alto Networks PCCSA Topics, Questions or Ask Anything Related
Free Palo Alto Networks PCCSA Exam Actual Questions
Note: Premium Questions for PCCSA were last updated On 03-06-2021 (see below)
Question #1
In the context of a mobile device management solution, what is a function of the ''policy enforcement'' feature?
Correct Answer:
A
Question #2
Question #3
What is the result of deploying virtualization in your data center?
Correct Answer:
B
Question #4
Which two remote access methods are secure because they encrypt traffic? (Choose two.)
Correct Answer:
B, C
Question #5
Assume that it is your responsibility to secure the software functioning at top five layers in the exhibit.
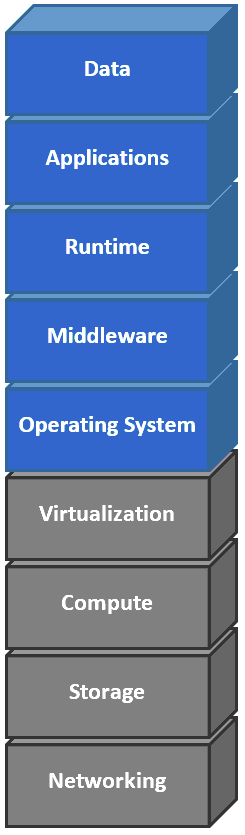
Which cloud service model type is represented?
Correct Answer:
C
Unlock Premium PCCSA Exam Questions with Advanced Practice Test Features:
- Select Question Types you want
- Set your Desired Pass Percentage
- Allocate Time (Hours : Minutes)
- Create Multiple Practice tests with Limited Questions
- Customer Support
Currently there are no comments in this discussion, be the first to comment!