Free Microsoft SC-100 Exam Dumps
Here you can find all the free questions related with Microsoft Cybersecurity Architect (SC-100) exam. You can also find on this page links to recently updated premium files with which you can practice for actual Microsoft Cybersecurity Architect Exam. These premium versions are provided as SC-100 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the Microsoft Cybersecurity Architect Exam premium files for free, Good luck with your Microsoft Cybersecurity Architect Exam.Hotspot
You have an Azure subscription and an on-premises datacenter. The datacenter contains 100 servers that run Windows Server. AJI the servers are backed up to a Recovery Services vault by using Azure Backup and the Microsoft Azure Recovery Services (MARS) agent.
You need to design a recovery solution for ransomware attacks that encrypt the on-premises servers. The solution must follow Microsoft Security Best Practices and protect against the following risks:
* A compromised administrator account used to delete the backups from Azure Backup before encrypting the servers
* A compromised administrator account used to disable the backups on the MARS agent before encrypting the servers
What should you use for each risk? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

DragDrop
You have a Microsoft 365 subscription
You need to recommend a security solution to monitor the following activities:
* User accounts that were potentially compromised
* Users performing bulk file downloads from Microsoft SharePoint Online
What should you include in the recommendation for each activity? To answer, drag the appropriate components to the correct activities. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each Correct selection is worth one Point.











https://docs.microsoft.com/en-us/microsoft-365/security/defender/investigate-users
DragDrop
You have a Microsoft 365 subscription
You need to recommend a security solution to monitor the following activities:
* User accounts that were potentially compromised
* Users performing bulk file downloads from Microsoft SharePoint Online
What should you include in the recommendation for each activity? To answer, drag the appropriate components to the correct activities. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each Correct selection is worth one Point.






MultipleChoice
Your company has a hybrid cloud infrastructure.
Data and applications are moved regularly between cloud environments.
The company's on-premises network is managed as shown in the following exhibit.
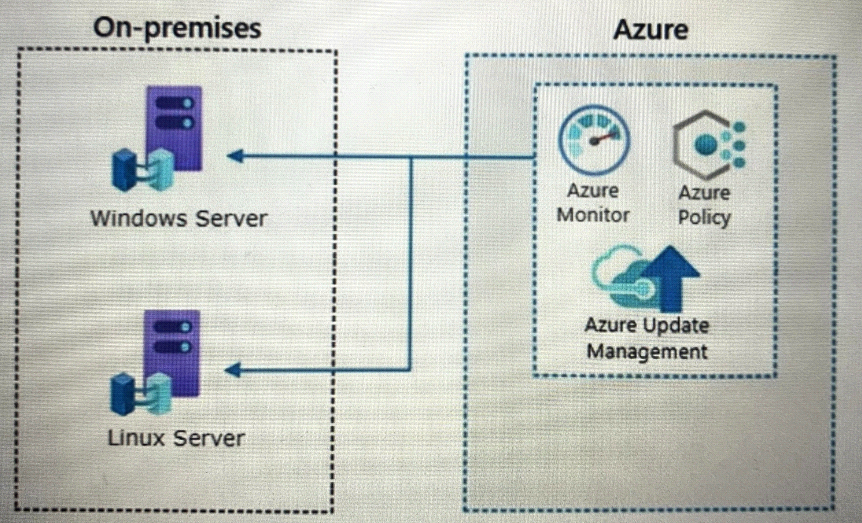
NOTE Each correct selection is worth one point.
OptionsMultipleChoice
A customer has a Microsoft 365 E5 subscription and an Azure subscription.
The customer wants to centrally manage security incidents, analyze log, audit activity, and hunt for potential threats across all deployed services.
You need to recommend a solution for the customer. The solution must minimize costs.
What should you include in the recommendation?
OptionsMultipleChoice
You have an Azure subscription that contains virtual machines, storage accounts, and Azure SQL databases. All resources are backed up multiple times a day by using Azure Backup. You are developing a strategy to protect against ransomware attacks.
You need to recommend which controls must be enabled to ensure that Azure Backup can be used to restore the resources in the event of a successtu\ ransonvwaTe
attack.
Which two controls should you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
OptionsMultipleChoice
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You need to enforce ISO 2700V2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatical
What should you use?
OptionsMultipleChoice
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation?
Options
