Microsoft AZ-100 Exam Questions
- Topic 1: Manage Azure Subscriptions and Resources
- Topic 2: Administrator Permissions/ Configure Azure Subscription Policies
- Topic 3: Analyze Resource Utilization and Consumption/ Diagnostic Setting on resources
- Topic 4: Creation of Baseline for Resources/ Rest Alerts
- Topic 5: Analyze Alerts Across Subscription/ Metrics Across Subscription Monitor of Unused Resources/ Report of Spend
- Topic 6: Utilize Log Search Query Functions
- Topic 7: Manage Resource Groups/ Azure Policies
- Topic 8: Configure Resource Locks and Policies
- Topic 9: Implement and Set Tagging on Resource Groups
- Topic 10: Move OR Remove across Resource Groups
Free Microsoft AZ-100 Exam Actual Questions
Note: Premium Questions for AZ-100 were last updated On 09-08-2019 (see below)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these
questions will not appear in the review screen.
You have a computer named Computer1 that has a point-to-site VPN connection to an Azure virtual network named VNet1. The point-to-site connection uses a self-signed certificate.
From Azure, you download and install the VPN client configuration package on a computer named Computer2.
You need to ensure that you can establish a point-to-site VPN connection to VNet1 from Computer2.
Solution: You modify the Azure Active Directory (Azure AD) authentication policies.
Does this meet this goal?
You have an Azure subscription named Subscription1 that contains a virtual network named VNet1. VNet1 is in a resource group named RG1.
Subscription1 has a user named User1. User1 has the following roles:
Reader
Security Admin
Security Reader
You need to ensure that User1 can assign the Reader role for VNet1 to other users.
What should you do?
You create an Azure subscription named Subscription1 and an associated Azure Active Directory (Azure AD) tenant named Tenant1.
Tenant1 contains the users in the following table.
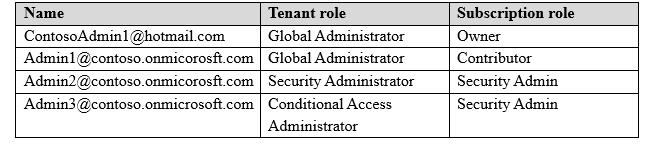
You need to add an Azure AD Privileged Identity Management application to Tenant1.
Which account can you use?
You have an Azure subscription named Subscription1 and two Azure Active Directory (Azure AD) tenants
named Tenant1 and Tenant2.
Subscription1 is associated to Tenant1. Multi-factor authentication (MFA) is enabled for all the users in
Tenant1.
You need to enable MFA for the users in Tenant2. The solution must maintain MFA for Tenant1.
What should you do first?
You have an Azure Active Directory (Azure AD) tenant.
You have an existing Azure AD conditional access policy named Policy1. Policy1 enforces the use of Azure AD-joined devices when members of the Global Administrators group authenticate to Azure AD from untrusted locations.
You need to ensure that members of the Global Administrators group will also be forced to use multi-factor authentication when authenticating from untrusted locations.
What should you do?
There are two types of controls:
Grant controls -- To gate access
Session controls -- To restrict access to a session
Grant controls oversee whether a user can complete authentication and reach the resource that they're attempting to sign-in to. If you have multiple controls selected, you can configure whether all of them are required when your policy is processed. The current implementation of Azure Active Directory enables you to set the following grant control requirements:
References:
https://blog.lumen21.com/2017/12/15/conditional-access-in-azure-active-directory/
- Select Question Types you want
- Set your Desired Pass Percentage
- Allocate Time (Hours : Minutes)
- Create Multiple Practice tests with Limited Questions
- Customer Support
Currently there are no comments in this discussion, be the first to comment!