Deal of The Day! Hurry Up, Grab the Special Discount - Save 25% - Ends In 00:00:00 Coupon code: SAVE25
Microsoft Exam MS-500 Topic 3 Question 20 Discussion
Actual exam question for
Microsoft's
MS-500 exam
Question #: 20
Topic #: 3
[All MS-500 Questions]
Topic #: 3
You create an Azure Sentinel workspace.
You configure Azure Sentinel to ingest data from Azure Active Directory (Azure AD).
In the Azure Active Directory admin center, you discover Azure AD Identity Protection alerts. The Azure Sentinel workspace shows the status as shown in the following exhibit.
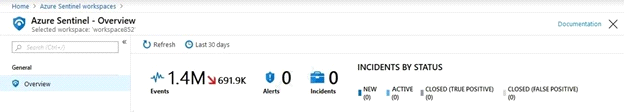
In Azure Log Analytics, you can see Azure AD data in the Azure Sentinel workspace.
What should you configure in Azure Sentinel to ensure that incidents are created for detected threats?
Suggested Answer:
B
Currently there are no comments in this discussion, be the first to comment!