Deal of The Day! Hurry Up, Grab the Special Discount - Save 25% - Ends In 00:00:00 Coupon code: SAVE25
Microsoft Exam MD-101 Topic 1 Question 53 Discussion
Actual exam question for
Microsoft's
MD-101 exam
Question #: 53
Topic #: 1
[All MD-101 Questions]
Topic #: 1
You have the devices shown in the following table.
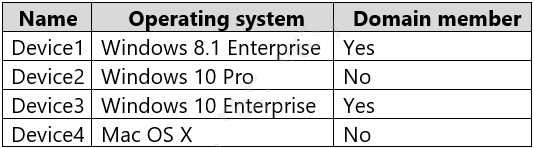
You plan to implement Microsoft Defender for Endpoint.
You need to identify which devices can be onboarded to Microsoft Defender for Endpoint.
What should you identify?
Currently there are no comments in this discussion, be the first to comment!