Free Microsoft AZ-500 Exam Dumps
Here you can find all the free questions related with Microsoft Azure Security Technologies (AZ-500) exam. You can also find on this page links to recently updated premium files with which you can practice for actual Microsoft Azure Security Technologies Exam. These premium versions are provided as AZ-500 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the Microsoft Azure Security Technologies Exam premium files for free, Good luck with your Microsoft Azure Security Technologies Exam.MultipleChoice
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Azure Username: User1-10598168@ExamUsers.com
Azure Password: Ag1Bh9!#Bd
The following information is for technical support purposes only:
Lab Instance: 10598168




You need to ensure that only devices connected to a 131.107.0.0/16 subnet can access data in the rg1lod10598168 Azure Storage account.
To complete this task, sign in to the Azure portal.
OptionsMultipleChoice
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Azure Username: User1-10598168@ExamUsers.com
Azure Password: Ag1Bh9!#Bd
The following information is for technical support purposes only:
Lab Instance: 10598168




You need to email an alert to a user named admin1@contoso.com if the average CPU usage of a virtual machine named VM1 is greater than 70 percent for a period of 15 minutes.
To complete this task, sign in to the Azure portal.
OptionsMultipleChoice
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Azure Username: User1-10598168@ExamUsers.com
Azure Password: Ag1Bh9!#Bd
The following information is for technical support purposes only:
Lab Instance: 10598168




You need to collect all the audit failure data from the security log of a virtual machine named VM1 to an Azure Storage account.
To complete this task, sign in to the Azure portal.
This task might take several minutes to complete You can perform other tasks while the task completes.
OptionsMultipleChoice
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Azure Username: User1-10598168@ExamUsers.com
Azure Password: Ag1Bh9!#Bd
The following information is for technical support purposes only:
Lab Instance: 10598168




You need to perform the following tasks:
Ensure that App10598168 is registered to Azure Active Directory (Azure AD).
Generate a password for App10598168.
To complete this task, sign in to the Azure portal.
OptionsMultipleChoice
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Azure Username: User1-10598168@ExamUsers.com
Azure Password: Ag1Bh9!#Bd
The following information is for technical support purposes only:
Lab Instance: 10598168




You need to create a new Azure Active Directory (Azure AD) directory named 10598168.onmicrosoft.com. The new directory must contain a user named user1@10598168.onmicrosoft.com who is configured to sign in by using Azure Multi-Factor Authentication (MFA).
To complete this task, sign in to the Azure portal.
OptionsHotspot
You have an Azure subscription mat contains a resource group named RG1. RG1 contains a storage account named storage1.
You have two custom Azure rotes named Role1 and Role2 that are scoped to RG1.
The permissions for Role1 are shown in the following JSON code.


:
Hotspot
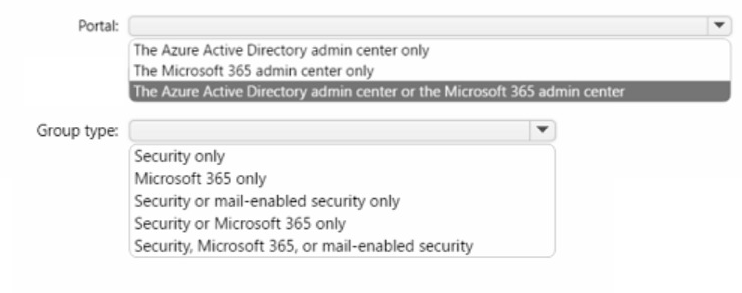
You have an Azure AD tenant named contoso.com that has Azure AD Premium P1 licenses.
You need to create a group named Group1 that will be assigned the Global reader role.
Which portal should you use to create Group1 and which type of group should you create? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point
https://learn.microsoft.com/en-us/azure/active-directory/roles/groups-create-eligible
OrderList
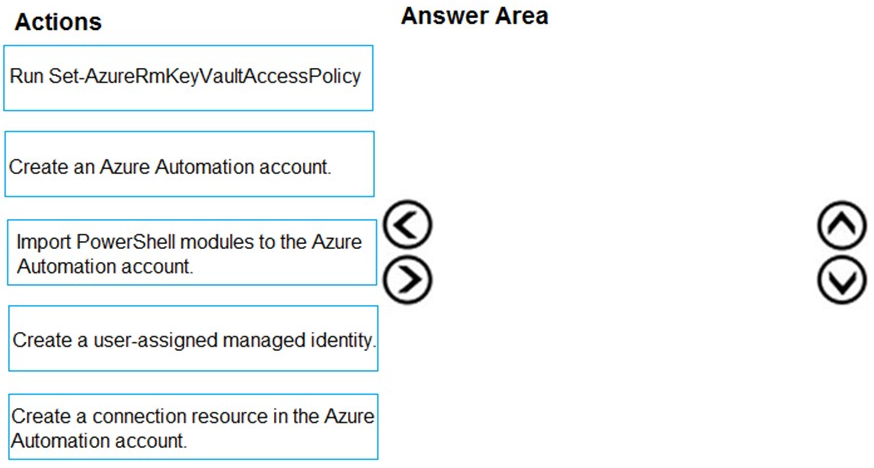
You have an Azure subscription named Sub1 that contains an Azure Storage account named Contosostorage1 and an Azure key vault named Contosokeyvault1.
You plan to create an Azure Automation runbook that will rotate the keys of Contosostorage1 and store them in Contosokeyvault1.
You need to implement prerequisites to ensure that you can implement the runbook.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Hotspot
Your company has an Azure subscription named Subscription1 that contains the users shown in the following table.

The company is sold to a new owner.
The company needs to transfer ownership of Subscription1.
Which user can transfer the ownership and which tool should the user use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

.
DragDrop
You have an Azure subscription named Sub1 that contains an Azure Log Analytics workspace named LAW1.
You have 500 Azure virtual machines that run Windows Server 2016 and are enrolled in LAW1.
You plan to add the System Update Assessment solution to LAW1.
You need to ensure that System Update Assessment-related logs are uploaded to LAW1 from 100 of the virtual machines only.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
















:

