Free HPE6-A73 Exam Dumps
Here you can find all the free questions related with HP Aruba Certified Switching Professional Exam (HPE6-A73) exam. You can also find on this page links to recently updated premium files with which you can practice for actual HP Aruba Certified Switching Professional Exam . These premium versions are provided as HPE6-A73 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the Aruba Certified Switching Professional Exam premium files for free, Good luck with your HP Aruba Certified Switching Professional Exam .MultipleChoice
A company has implemented 802 1X authentication on AOS-CX access switches, where two ClearPass servers are used to implement AAA Each switch has the two servers defined A network engineer notices the following command configured on the AOS'CX switches:
radius-server tracking user-name monitor password plaintext arubal23
What is the purpose of this configuration?
OptionsMultipleChoice
A network engineer is examining NAE graphs from the Dashboard but notices that the time shown in the graph does not represent the current time The engineer verifies that the AOS-CX switch is configured for NTP and is successfully synchronized. What should be done to fix this issue?
OptionsMultipleChoice
An administrator creates an ACL rule with both the "count" and "log'; option enabled What is correct about the action taken by an AOS-CX switch when there is a match on this rule?
OptionsMultipleChoice
An administrator is replacing the current access switches with AOS-CX switches. The access layer switches must authenticate user and networking devices connecting to them. Some devices support no form of authentication and some support S02 1X Some ports have a VoIP phone and a PC connected to the same port where the PC is connected to the data port of the phone and the phone's LAN port is connected to the switch.
Which statement is correct about this situation?
OptionsMultipleChoice
Examine the following ACL rule policies:
* Permit traffic from 10.2.2.1 through 10.2.2.30 to anywhere
* Permit traffic from 10 2.2 40 through 10 2 2 55 to anywhere
* Deny all others
Based on this policy, place the following ACL rule statements in the correct order to accomplish the above filtering policy.
OptionsMultipleChoice
Refer to the exhibit.
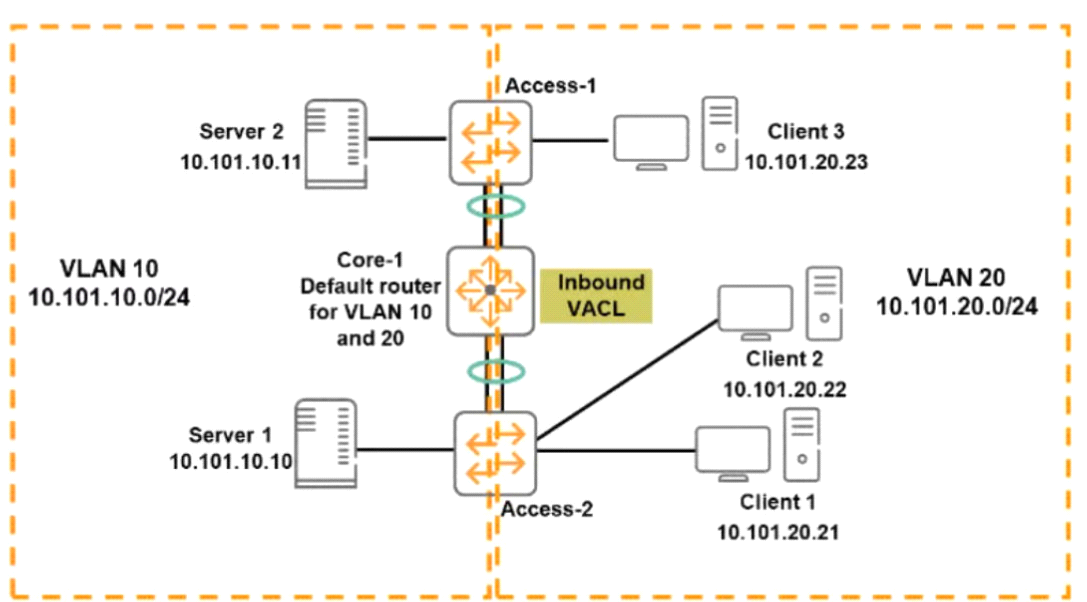
The ACL configuration defined on Core-1 is as follows:
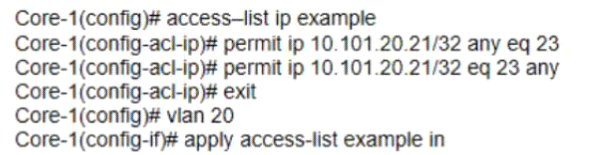
if telnet was being used which device connection would he permitted and functional in both directions? (Select two }
OptionsMultipleChoice
How does PIM build the IP multicast routing table to route traffic between a multicast source and one or more receivers9
OptionsMultipleChoice
A company has an existing wireless solution involving Aruba APs and Mobility controllers running 8 4 code The solution
leverages a third-party AAA solution. The company is replacing existing access switches with AOS-CX 6300 and 6400
switches The company wants to leverage the same security and firewall policies for both wired and wireless traffic.
Which solution should the company implement?
OptionsMultipleChoice
How js voice traffic prioritized correctly on AOS-CX switches'?
OptionsMultipleChoice
The two PCs are located in VLAN 11 (10 1 11 0/24} Which example defines how to implement active gateway on the vsx core for VLAN 11?
A)
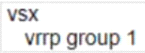
B)
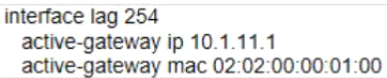
C)
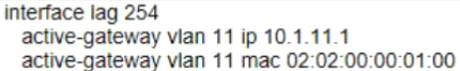
D)
Options
