Deal of The Day! Hurry Up, Grab the Special Discount - Save 25% - Ends In 00:00:00 Coupon code: SAVE25
HPE6-A29 Exam Questions
Status: RETIRED
Exam Name: Aruba Certified Mobility Professional
Exam Code:
HPE6-A29
Related Certification(s): HP Aruba Certified Mobility Professional ACMP V6.4 Certification
Certification Provider: HP
Actual Exam Duration: 90 Minutes
Number of HPE6-A29 practice questions in our database:
301
(updated: 25-09-2019)
Expected HPE6-A29 Exam Topics, as suggested by HP :
- Topic 1: Describe the functions
- Topic 2: features
- Topic 3: and capabilities of HPE SDN solutions
- Topic 4: Describe the Design and configure multi-controller networks with redundancy and mobility
- Topic 5: Define theparticular customer requirement
- Topic 6: recommend an HPE SDN solution.
Disscuss HP HPE6-A29 Topics, Questions or Ask Anything Related
Free HP HPE6-A29 Exam Actual Questions
Note: Premium Questions for HPE6-A29 were last updated On 25-09-2019 (see below)
Question #1
Which two factors are important when choosing a controller model to support tunneled node?
Correct Answer:
A, C
Question #2
Exhibit:
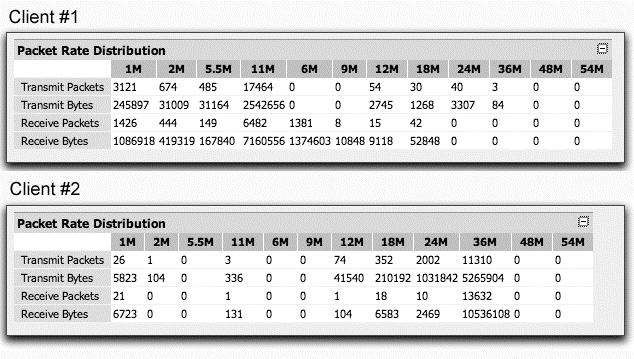
Referring to the screen captures provided for this question, what can you conclude about the two clients from the Packet Rate Distribution screens?
Correct Answer:
C
Question #3
Which of the following functions cannot be done in the offline Visual RF plan?
Correct Answer:
C
Question #4
A Remote AP provisioned with an SSID in the operational mode always has which one of the following characteristics?
Correct Answer:
C
Question #5
As illustrated in the above diagram and screen capture, a wireless hacker injects messages into your network to detach a client from your Aruba AP.
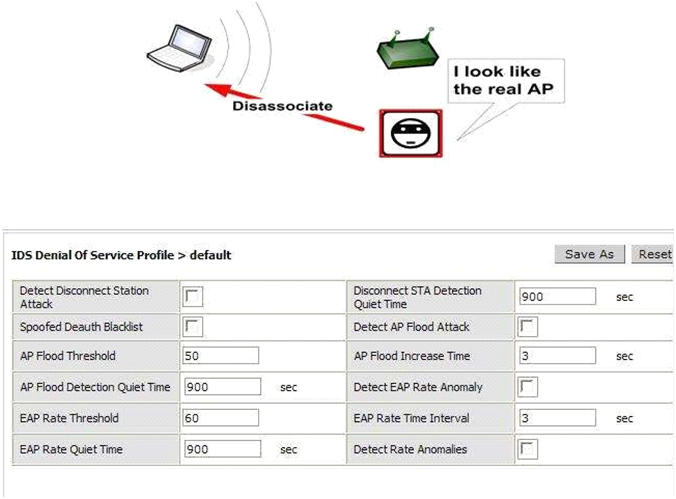
What action should you take to identify and prevent the Intruder from connecting to your system?
Correct Answer:
A, B
Unlock Premium HPE6-A29 Exam Questions with Advanced Practice Test Features:
- Select Question Types you want
- Set your Desired Pass Percentage
- Allocate Time (Hours : Minutes)
- Create Multiple Practice tests with Limited Questions
- Customer Support
Currently there are no comments in this discussion, be the first to comment!