Deal of The Day! Hurry Up, Grab the Special Discount - Save 25% - Ends In 00:00:00 Coupon code: SAVE25
GAQM Exam CPEH-001 Topic 6 Question 51 Discussion
Actual exam question for
GAQM's
CPEH-001 exam
Question #: 51
Topic #: 6
[All CPEH-001 Questions]
Topic #: 6
Joe the Hacker breaks into XYZ's Linux system and plants a wiretap program in order to sniff passwords and user accounts off the wire. The wiretap program is embedded as a Trojan horse in one of the network utilities. Joe is worried that network administrator might detect the wiretap program by querying the interfaces to see if they are running in promiscuous mode.
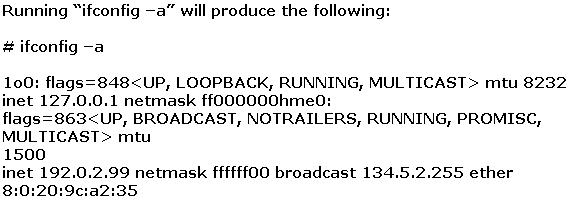
What can Joe do to hide the wiretap program from being detected by ifconfig command?
Suggested Answer:
C
The normal way to hide these rogue programs running on systems is the use crafted commands like ifconfig and ls.
Currently there are no comments in this discussion, be the first to comment!