Deal of The Day! Hurry Up, Grab the Special Discount - Save 25% - Ends In 00:00:00 Coupon code: SAVE25
GAQM Exam CPEH-001 Topic 3 Question 18 Discussion
Actual exam question for
GAQM's
CPEH-001 exam
Question #: 18
Topic #: 3
[All CPEH-001 Questions]
Topic #: 3
ETHER: Destination address : 0000BA5EBA11 ETHER: Source address :
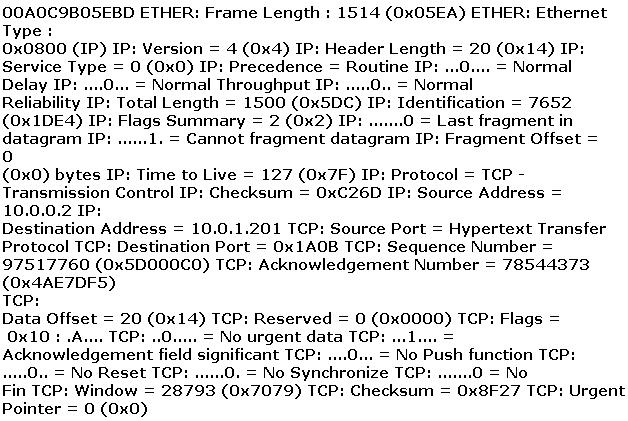
An employee wants to defeat detection by a network-based IDS application. He does not want to attack the system containing the IDS application. Which of the following strategies can be used to defeat detection by a network-based IDS application?
Suggested Answer:
B
Certain types of encryption presents challenges to network-based intrusion detection and may leave the IDS blind to certain attacks, where a host-based IDS analyzes the data after it has been decrypted.
Currently there are no comments in this discussion, be the first to comment!