Free Fortinet NSE4_FGT-6.4 Exam Dumps
Here you can find all the free questions related with Fortinet NSE4_FGT-6.4: Fortinet NSE 4 - FortiOS 6.4 (NSE4_FGT-6.4) exam. You can also find on this page links to recently updated premium files with which you can practice for actual Fortinet NSE4_FGT-6.4: Fortinet NSE 4 - FortiOS 6.4 Exam. These premium versions are provided as NSE4_FGT-6.4 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the NSE4_FGT-6.4: Fortinet NSE 4 - FortiOS 6.4 Exam premium files for free, Good luck with your Fortinet NSE4_FGT-6.4: Fortinet NSE 4 - FortiOS 6.4 Exam.MultipleChoice
Refer to the exhibit.
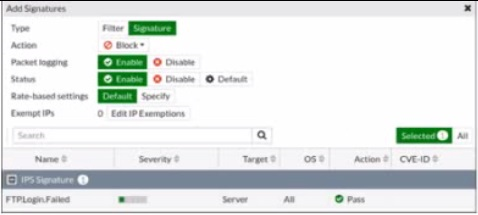
Review the Intrusion Prevention System (IPS) profile signature settings. Which statement is correct in adding the FTP.Login.Failed signature to the IPS sensor profile?
OptionsMultipleChoice
View the exhibit.
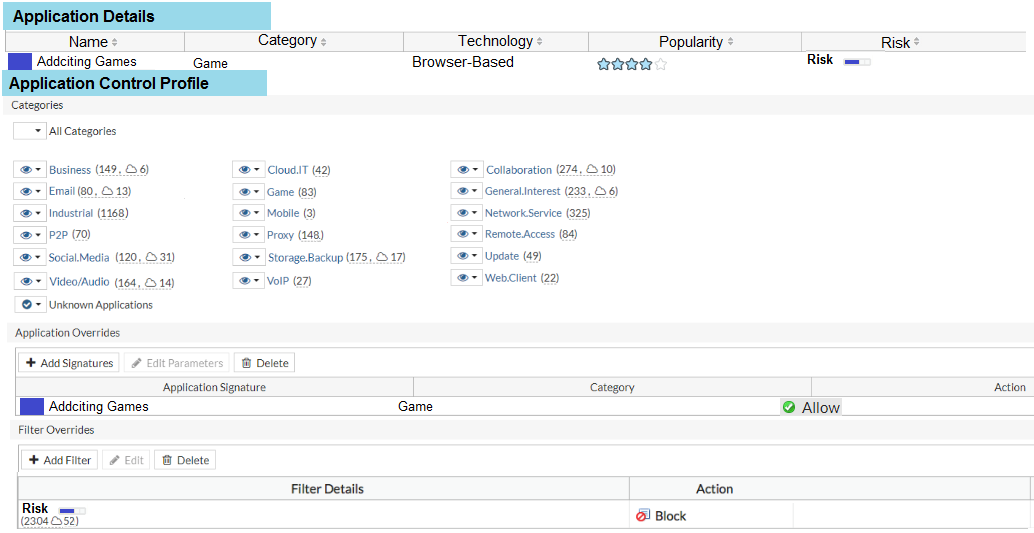
A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting Games). Based on this configuration, which statement is true?
OptionsMultipleChoice
Refer to the exhibit.
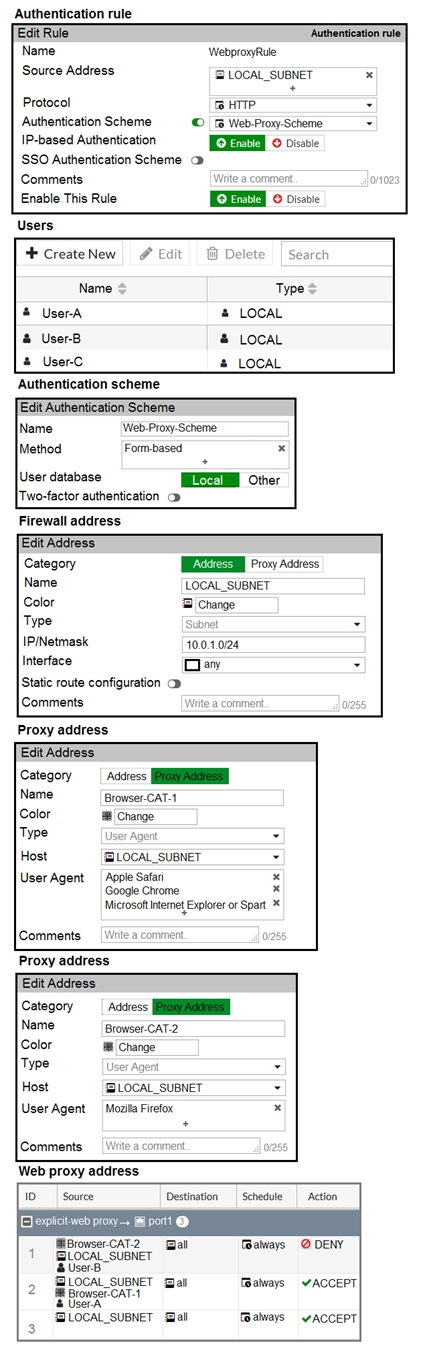
The exhibit shows proxy policies and proxy addresses, the authentication rule and authentication scheme, users, and firewall address.
An explicit web proxy is configured for subnet range 10.0.1.0/24 with three explicit web proxy policies.
The authentication rule is configured to authenticate HTTP requests for subnet range 10.0.1.0/24 with a form-based authentication scheme for the FortiGate local user database. Users will be prompted for authentication.
How will FortiGate process the traffic when the HTTP request comes from a machine with the source IP 10.0.1.10 to the destination http://www.fortinet.com? (Choose two.)
OptionsMultipleChoice
An administrator Is configuring an IPsec VPN between site A and site B. The Remote Gateway setting in both sites has been configured as Static IP Address. For site
OptionsMultipleChoice
Refer to the exhibit.
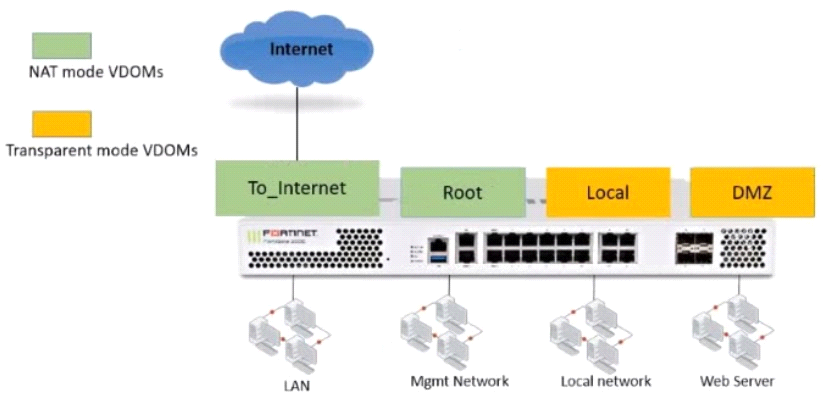
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access internet. The To_lnternet VDOM is the only VDOM with internet access and is directly connected to ISP modem.
Which two statements are true? (Choose two.)
OptionsMultipleChoice
Which statement about the policy ID number of a firewall policy is true?
D18912E1457D5D1DDCBD40AB3BF70D5D
OptionsMultipleChoice
D18912E1457D5D1DDCBD40AB3BF70D5D
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
Options
