Deal of The Day! Hurry Up, Grab the Special Discount - Save 25% - Ends In 00:00:00 Coupon code: SAVE25
Eccouncil Exam 312-39 Topic 9 Question 57 Discussion
Actual exam question for
Eccouncil's
312-39 exam
Question #: 57
Topic #: 9
[All 312-39 Questions]
Topic #: 9
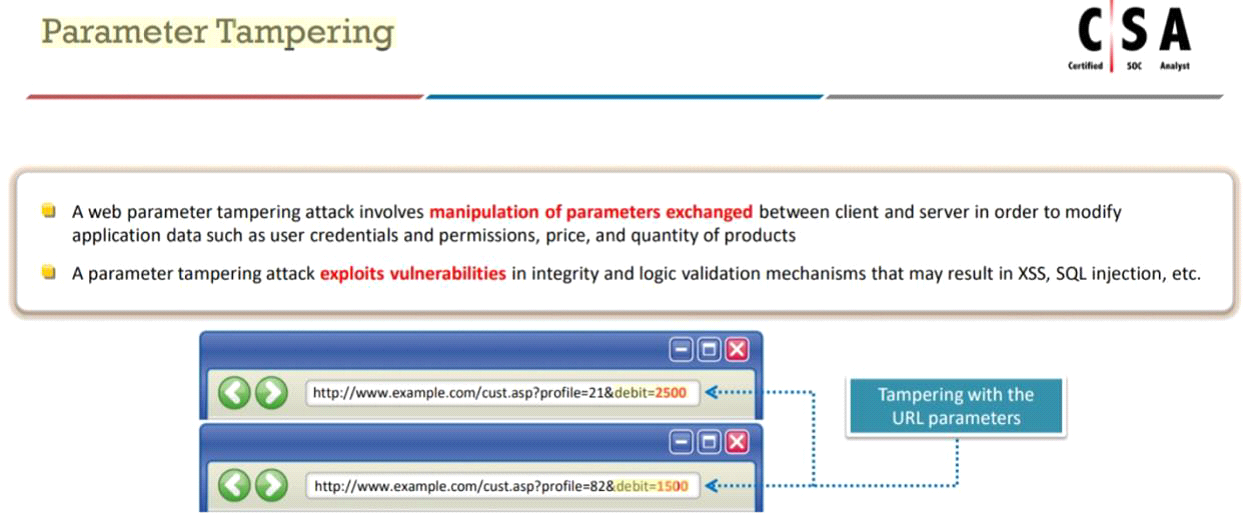
An attacker exploits the logic validation mechanisms of an e-commerce website. He successfully purchases a product worth $100 for $10 by modifying the URL exchanged between the client and the server.
Identify the attack depicted in the above scenario.
Suggested Answer:
C
Currently there are no comments in this discussion, be the first to comment!