Free Eccouncil 312-38 Exam Dumps
Here you can find all the free questions related with Eccouncil Certified Network Defender (312-38) exam. You can also find on this page links to recently updated premium files with which you can practice for actual Eccouncil Certified Network Defender Exam. These premium versions are provided as 312-38 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the Certified Network Defender Exam premium files for free, Good luck with your Eccouncil Certified Network Defender Exam.MultipleChoice
Which of the following protocols permits users to enter a user-friendly computer name into the Windows browser and to map network drives and view shared folders?
OptionsMultipleChoice
Which of the following attacks are computer threats that try to exploit computer application vulnerabilities that are unknown to others or undisclosed to the software developer? Each correct answer represents a complete solution. Choose all that apply.
OptionsMultipleChoice
Which of the following is the best way of protecting important data against virus attack?
OptionsMultipleChoice
Which of the following is a service discovery protocol that allows computers and other devices to find services in a local area network without prior configuration?
OptionsFillInTheBlank
s with the appropriate terms. In L2TP ______________ tunnel mode, the ISP must support L2TP, whereas in L2TP tunnel mode, the ISP does not need to support L2TP.
MultipleChoice
Jason works as a System Administrator for www.company.com Inc. The company has a Windows-based network. Sam, an employee of the company, accidentally changes some of the applications and system settings. He complains to Jason that his system is not working properly. To troubleshoot the problem, Jason diagnoses the internals of his computer and observes that some changes have been made in Sam's computer registry. To rectify the issue, Jason has to restore the registry. Which of the following utilities can Jason use to accomplish the task? Each correct answer represents a complete solution. Choose all that apply.
OptionsMultipleChoice
Adam works as a Security Analyst for Umbrella Inc. The company has a Linux-based network comprising an Apache server for Web applications. He received the following Apache Web server log, which is as follows:
[Sat Nov 16 14:32:52 2009] [error] [client 128.0.0.7] client denied by server configuration: /export/home/htdocs/test
The first piece in the log entry is the date and time of the log message. The second entry determines the severity of the error being reported.
Now Adam wants to change the severity level to control the types of errors that are sent to the error log. Which of the following directives will Adam use to accomplish the task?
OptionsMultipleChoice
Which of the following strategies is used to minimize the effects of a disruptive event on a company, and is created to prevent interruptions to normal business activity?
OptionsMultipleChoice
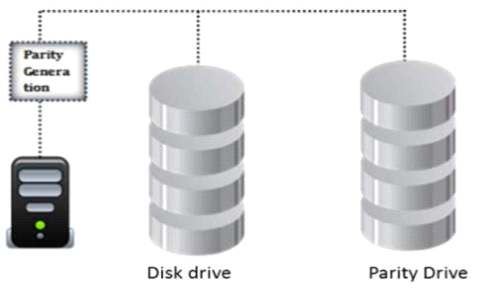
Identify the minimum number of drives required to setup RAID level 5.