Free CompTIA PT0-002 Exam Dumps
Here you can find all the free questions related with CompTIA PenTest+ Certification Exam (PT0-002) exam. You can also find on this page links to recently updated premium files with which you can practice for actual CompTIA PenTest+ Certification Exam . These premium versions are provided as PT0-002 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the CompTIA PenTest+ Certification Exam premium files for free, Good luck with your CompTIA PenTest+ Certification Exam .MultipleChoice
A penetration tester has been provided with only the public domain name and must enumerate additional information for the public-facing assets.
INSTRUCTIONS
Select the appropriate answer(s), given the output from each section.
Output 1






MultipleChoice
You are a penetration tester running port scans on a server.
INSTRUCTIONS
Part 1: Given the output, construct the command that was used to generate this output from the available options.
Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


MultipleChoice
A penetration tester discovers that a web server within the scope of the engagement has already been compromised with a backdoor. Which of the following should the penetration tester do NEXT?
OptionsMultipleChoice
The results of an Nmap scan are as follows:
Nmap scan report for ( 10.2.1.22 )
Host is up (0.0102s latency).
Not shown: 998 filtered ports
Port State Service
80/tcp open http
|_http-title: 80F 22% RH 1009.1MB (text/html)
|_http-slowloris-check:
| VULNERABLE:
| Slowloris DoS Attack
| <..>
Device type: bridge|general purpose
Running (JUST GUESSING) : QEMU (95%)
OS CPE: cpe:/a:qemu:qemu
No exact OS matches found for host (test conditions non-ideal).
Nmap done: 1 IP address (1 host up) scanned in 107.45 seconds
Which of the following device types will MOST likely have a similar response? (Choose two.)
OptionsMultipleChoice
Using the output, identify potential attack vectors that should be further investigated.
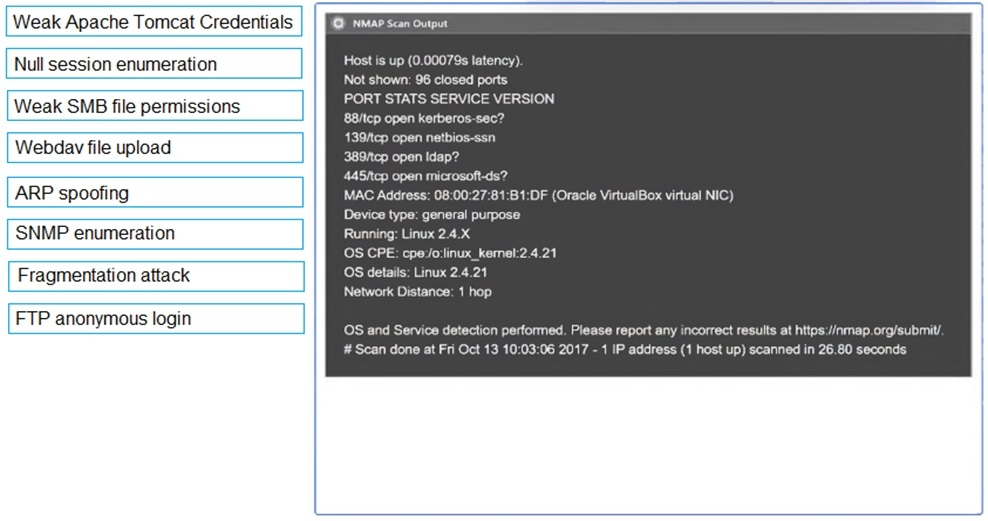
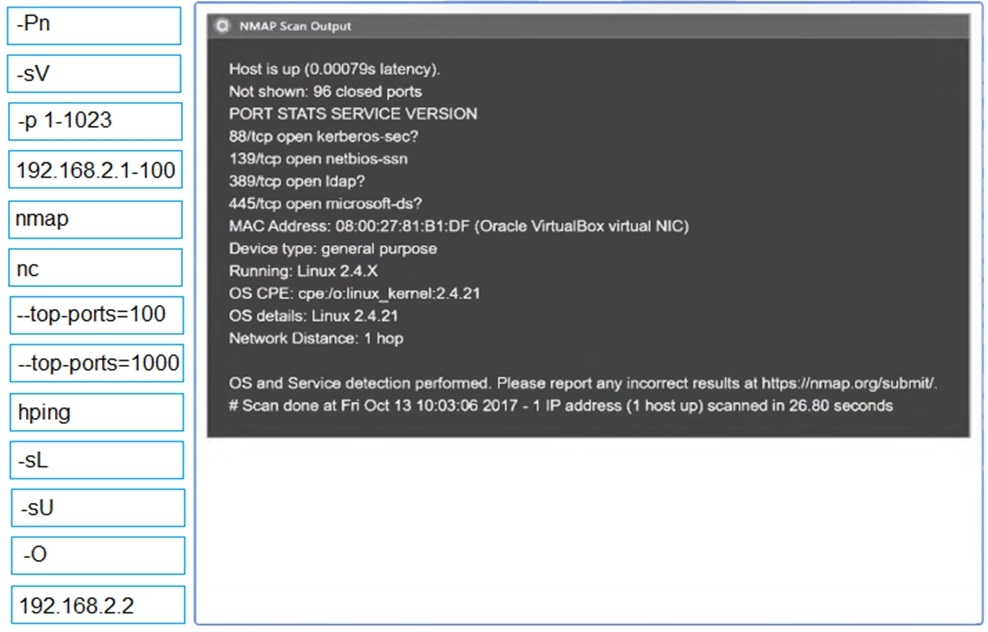
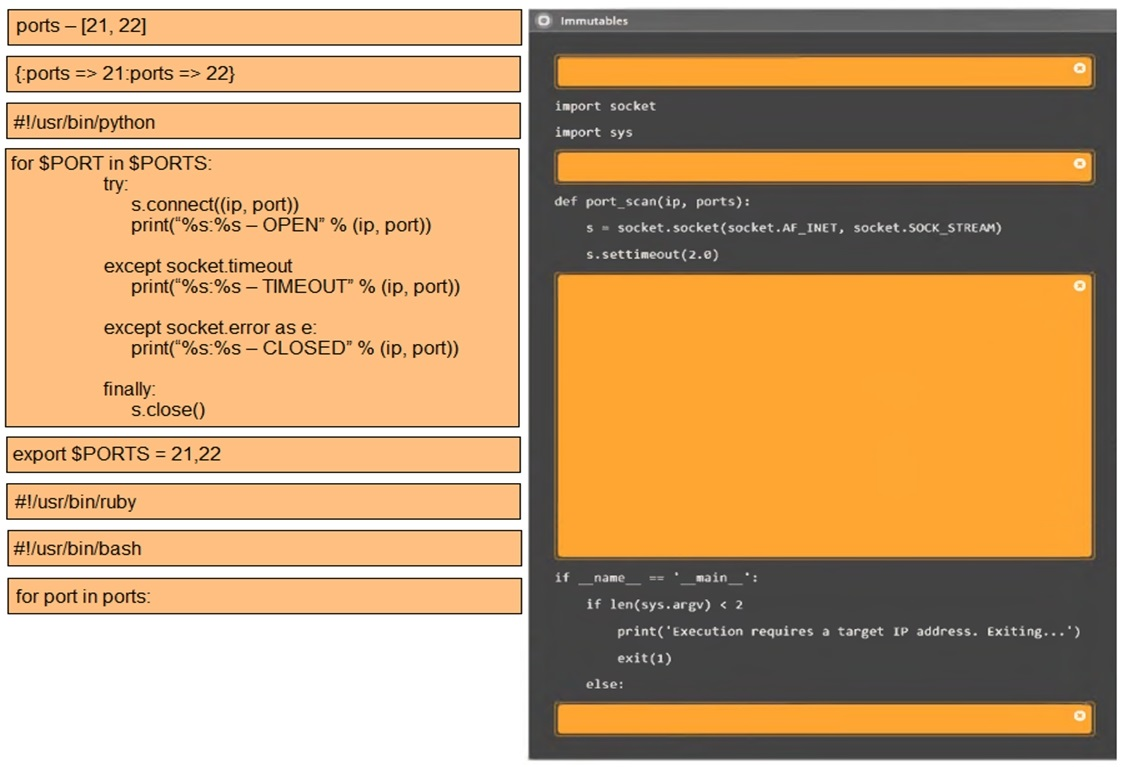
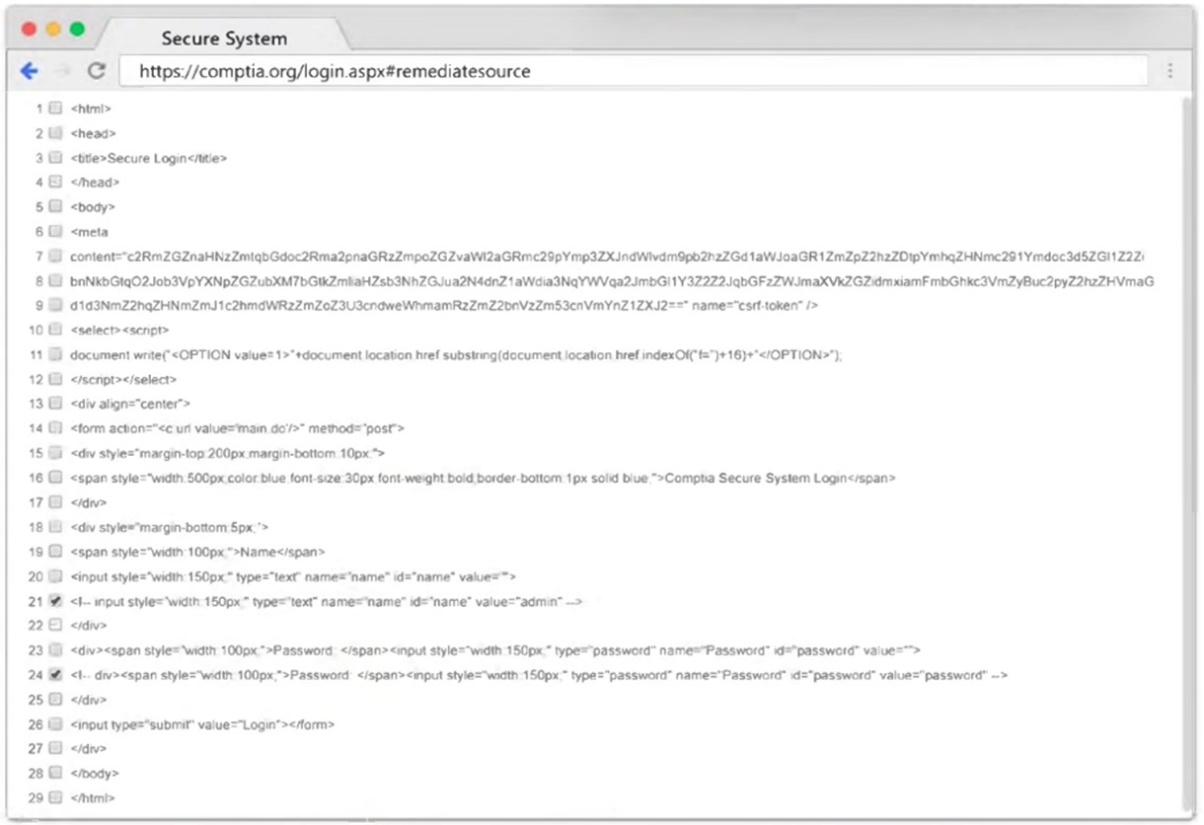
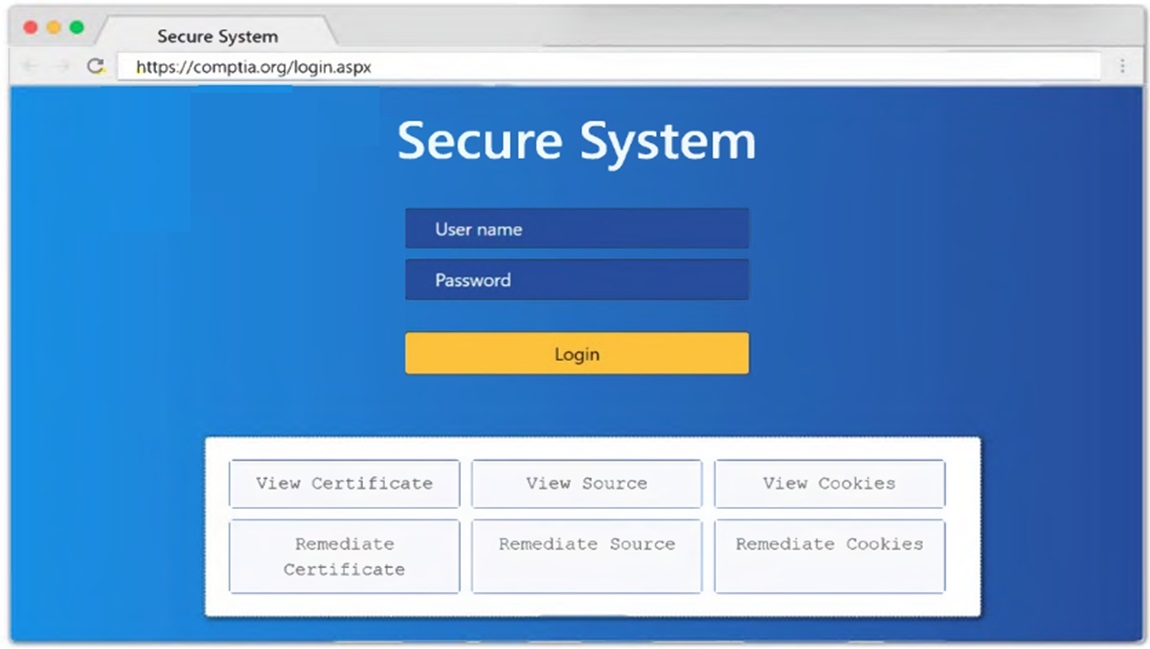
MultipleChoice
A penetration tester was brute forcing an internal web server and ran a command that produced the following output:
Which of the following is the MOST likely reason for the lack of output?
OptionsMultipleChoice
A penetration tester conducted an assessment on a web server. The logs from this session show the following:
Which of the following attacks is being attempted?
OptionsMultipleChoice
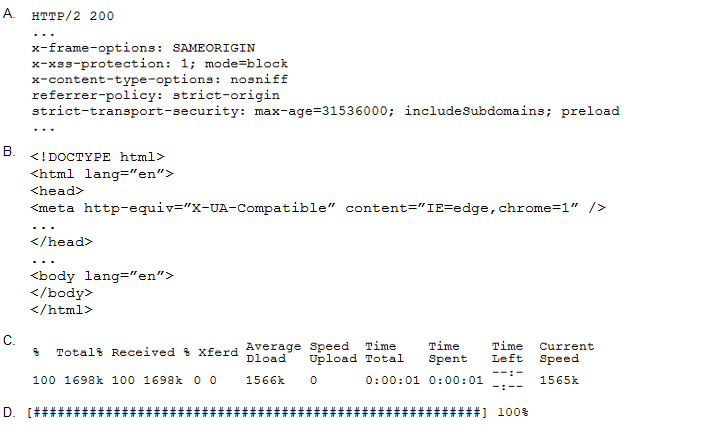
A penetration tester performs the following command:
Which of the following snippets of output will the tester MOST likely receive?
MultipleChoice
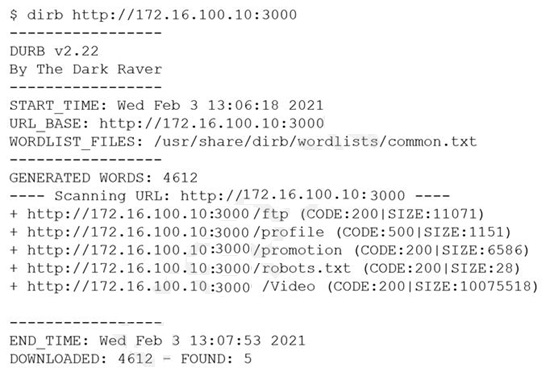
A penetration tester obtained the following results after scanning a web server using the dirb utility:
...
GENERATED WORDS: 4612
...
DOWNLOADED: 4612 -- FOUND: 4
Which of the following elements is MOST likely to contain useful information for the penetration tester?
Options
