Deal of The Day! Hurry Up, Grab the Special Discount - Save 25% - Ends In 00:00:00 Coupon code: SAVE25
CompTIA Exam CS0-002 Topic 2 Question 20 Discussion
Actual exam question for
CompTIA's
CS0-002 exam
Question #: 20
Topic #: 2
[All CS0-002 Questions]
Topic #: 2
An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output:
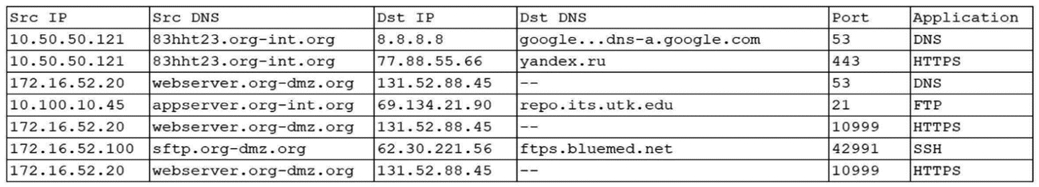
Which of the following should be the focus of the investigation?
Suggested Answer:
D
Currently there are no comments in this discussion, be the first to comment!