Independence Day Deal! Unlock 25% OFF Today – Limited-Time Offer - Ends In 00:00:00 Coupon code: SAVE25
CompTIA Exam CS0-001 Topic 13 Question 30 Discussion
Actual exam question for
CompTIA's
CS0-001 exam
Question #: 30
Topic #: 13
[All CS0-001 Questions]
Topic #: 13
A system administrator is doing network reconnaissance of a company's external network to determine the vulnerability of various services that are running. Sending some sample traffic to the external host, the administrator obtains the following packet capture:
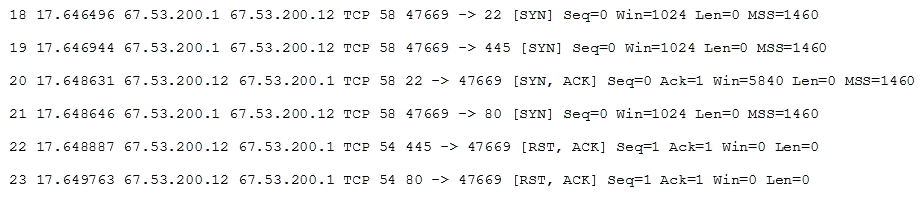
Based on the output, which of the following services should be further tested for vulnerabilities?
Suggested Answer:
C
Currently there are no comments in this discussion, be the first to comment!