Independence Day Deal! Unlock 25% OFF Today – Limited-Time Offer - Ends In 00:00:00 Coupon code: SAVE25
CompTIA Exam CAS-003 Topic 11 Question 43 Discussion
Actual exam question for
CompTIA's
CAS-003 exam
Question #: 43
Topic #: 11
[All CAS-003 Questions]
Topic #: 11
A company hosts a web-based application that is accessed by customers worldwide. A code review has discovered known vulnerabilities in the company's server application, which is made up of several supporting libraries and uses the following requirements:
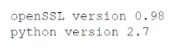
Additionally, Python imports are requirements.txt file with the following content:
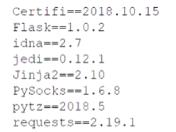
Given the critical nature of the application, which of the following actions should the company take to address the vulnerabilities?
Suggested Answer:
C
Currently there are no comments in this discussion, be the first to comment!