Free CompTIA 220-1102 Exam Dumps
Here you can find all the free questions related with CompTIA A+ Core 2 Exam (220-1102) exam. You can also find on this page links to recently updated premium files with which you can practice for actual CompTIA A+ Core 2 Exam . These premium versions are provided as 220-1102 exam practice tests, both as desktop software and browser based application, you can use whatever suits your style. Feel free to try the CompTIA A+ Core 2 Exam premium files for free, Good luck with your CompTIA A+ Core 2 Exam .MultipleChoice
A technician has verified that a user's computer has a virus, and the antivirus software is out Of date. Which of the following steps should the technician take NEXT?
OptionsMultipleChoice
A technician receives a call from a user who is on vacation. The user provides the necessary credentials and asks the technician to log in to the users account and read a critical email that the user has been expecting. The technician refuses because this is a violation of the:
OptionsMultipleChoice
As a corporate technician, you are asked to evaluate several suspect email messages on
a client's computer. Corporate policy requires he following:
. All phishing attempts must be reported.
. Future spam emails to users must be prevented.
INSTRUCTIONS
Review each email and perform the
following within the email:
. Classify the emails
. Identify suspicious items, if applicable, in each email
. Select the appropriate resolution

MultipleChoice
A user reports that after a recent software deployment to upgrade applications, the user can no longer use the Testing program.
However, other employees can successfully use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve any issues discovered by selecting the:
Index number of the Event Viewer issue
First command to resolve the issue
Second command to resolve the issue
BSOD

Commands:

Event Viewer:

System Error:



MultipleChoice
Ann, a CEO, has purchased a new consumer-class tablet for personal use, but she is unable to connect it to the company's wireless network. All the corporate laptops are connecting without issue. She has asked you to assist with getting the device online.
INSTRUCTIONS
Review the network diagrams and device configurations to determine the cause of the problem and resolve any discovered issues.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.









MultipleChoice
Which of the following security methods supports the majority of current WI-Fl---capable devices Without sacrificing security?
OptionsMultipleChoice
A technician needs lo formal a USB drive to transfer 20GB of data from a Linux computer to a Windows computer. Which of the following filesystems will the technician MOST likely use?
OptionsHotspot
Ann, a CEO, has purchased a new consumer-class tablet for personal use, but she is unable to connect it to the company's wireless network. All the corporate laptops are connecting without issue. She has asked you to assist with getting the device online.
INSTRUCTIONS
Review the network diagrams and device configurations to determine the cause of the problem and resolve any discovered issues.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
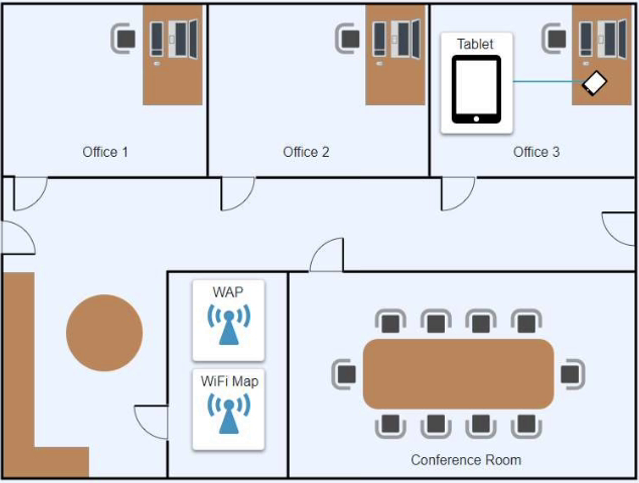
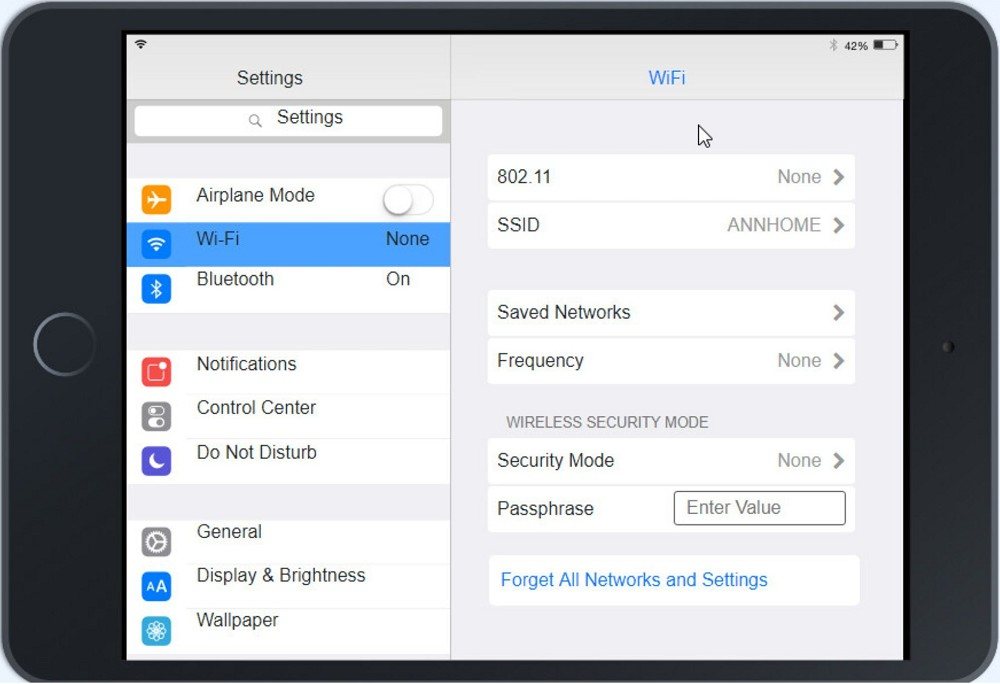
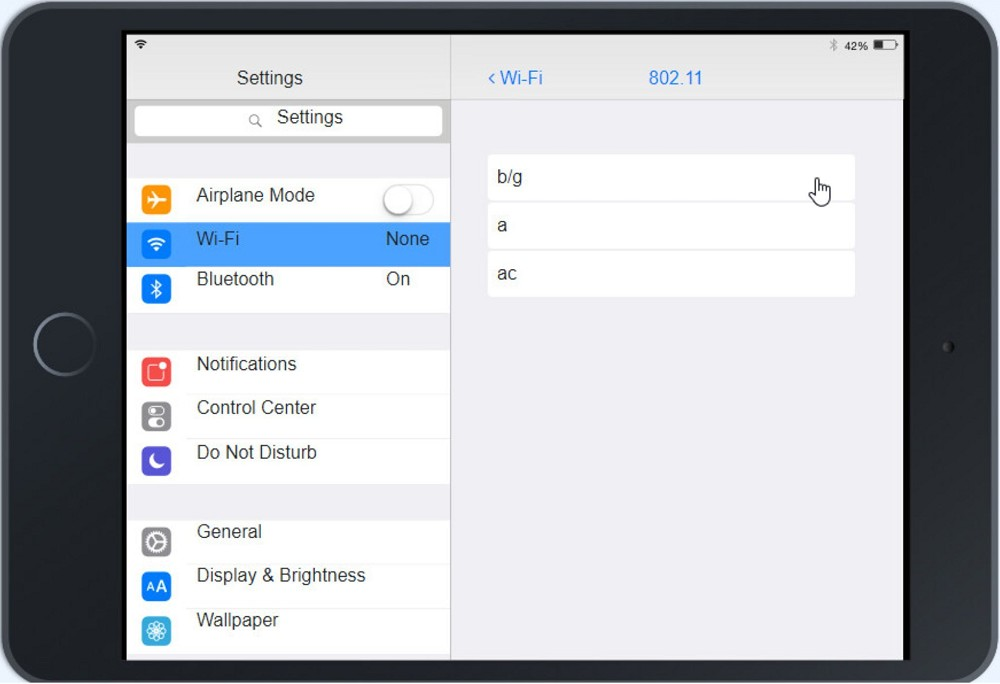
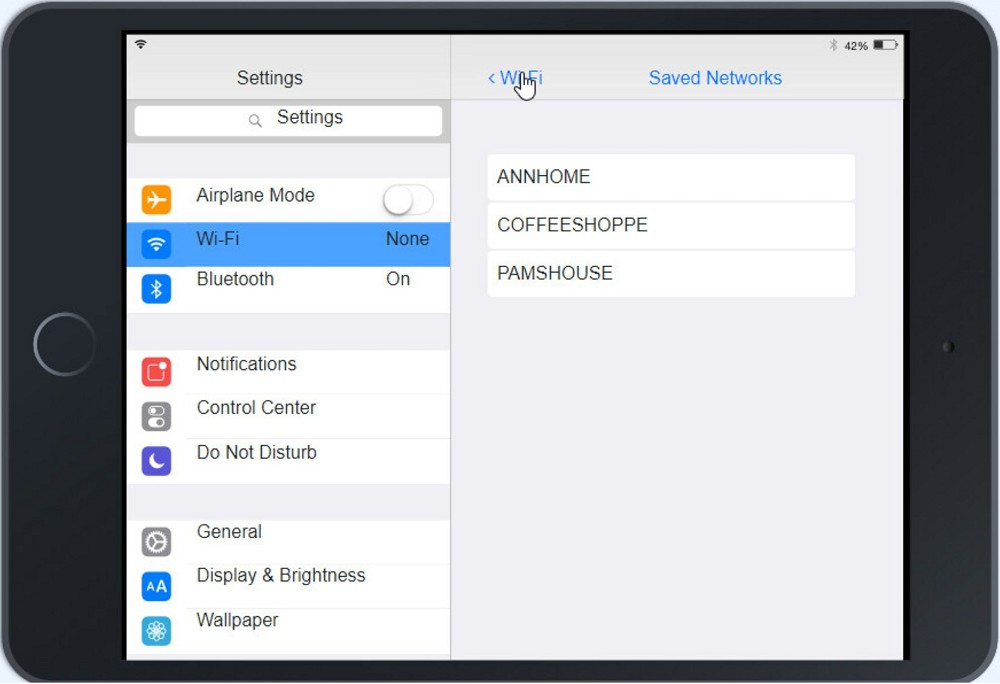
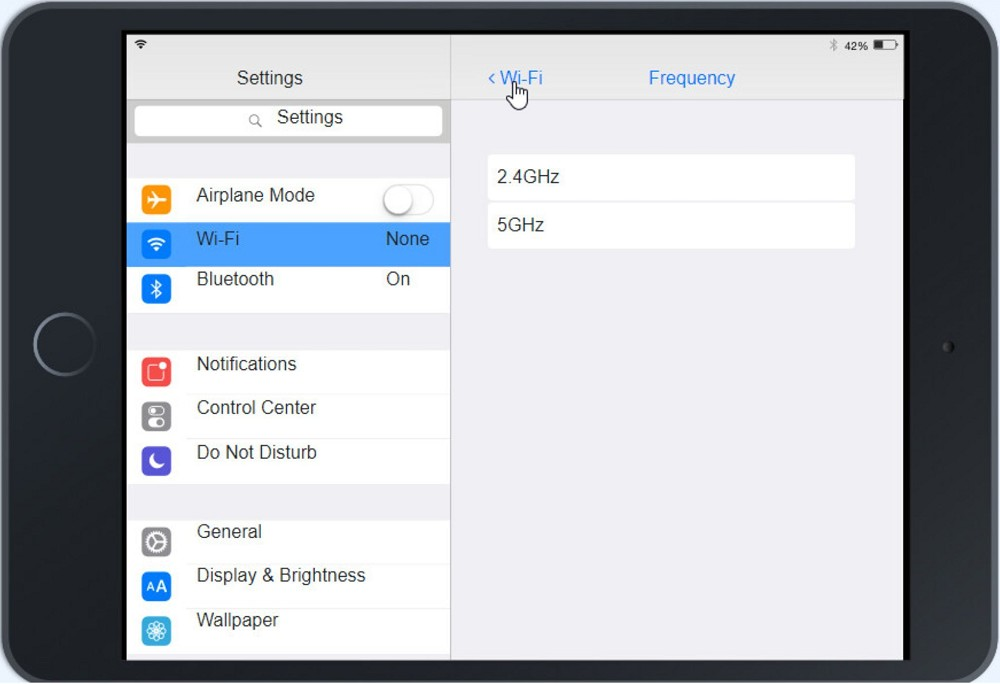
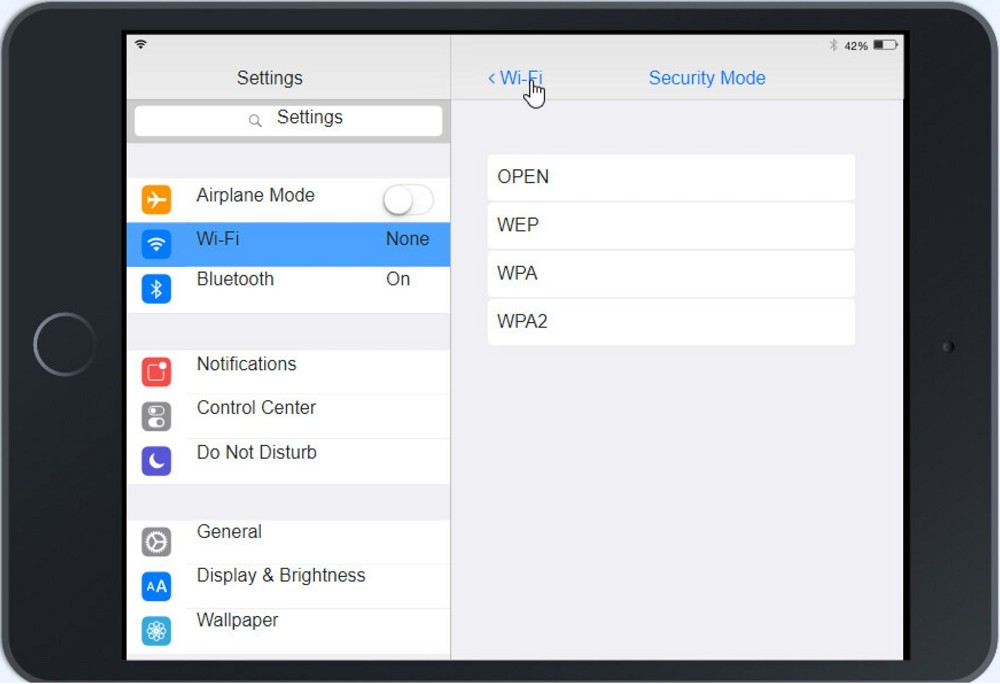
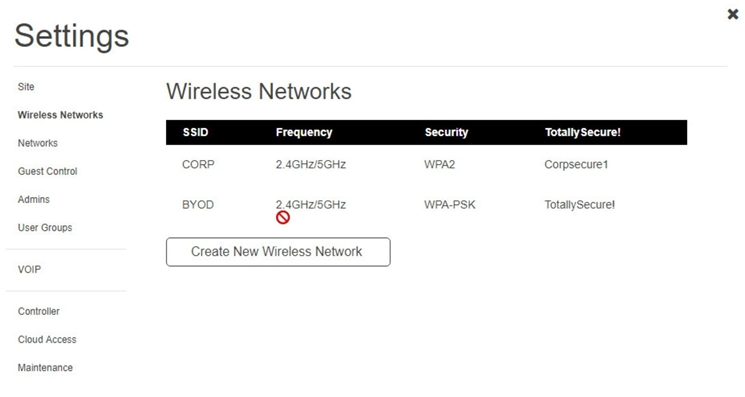
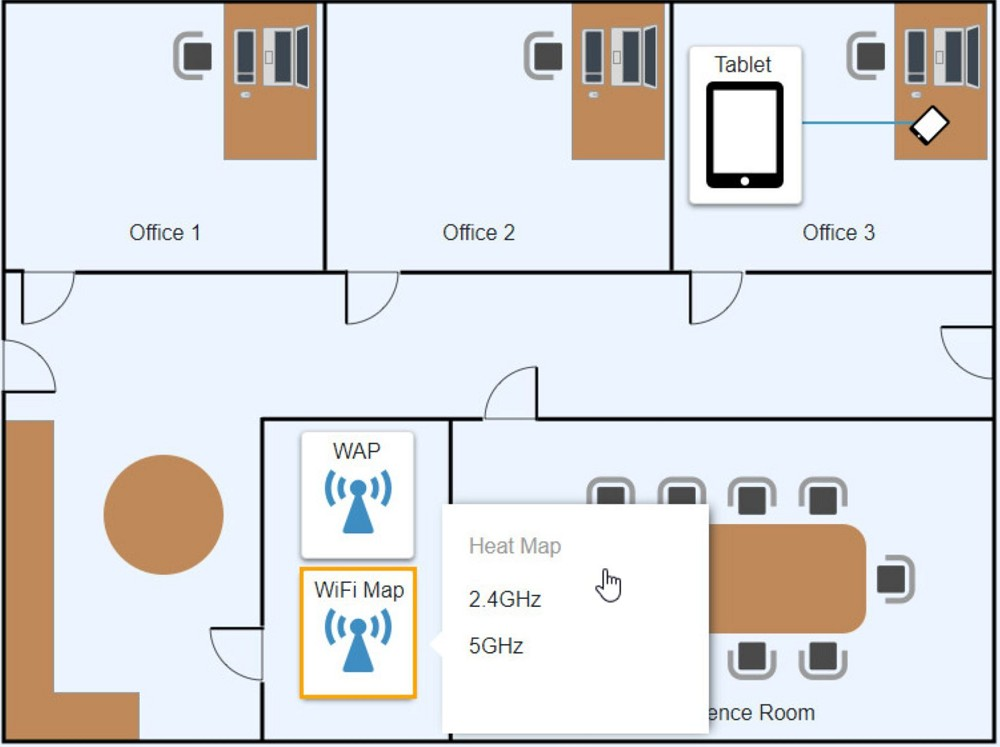
Click on 802.11 and Select ac
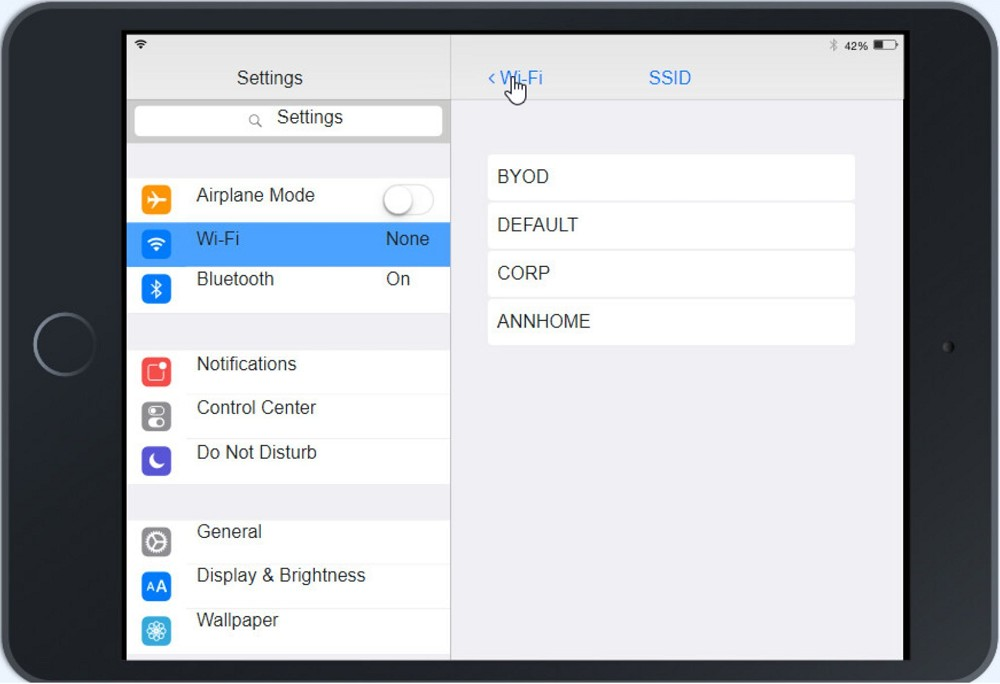
Click on SSID and select CORP
Click on Frequency and select 5GHz
At Wireless Security Mode, Click on Security Mode
Select the WPA2
Ann needs to connect to the BYOD SSID, using 2.4GHZ. The selected security method chose should be WPA PSK, and the password should be set to TotallySecret.
MultipleChoice
multichoice
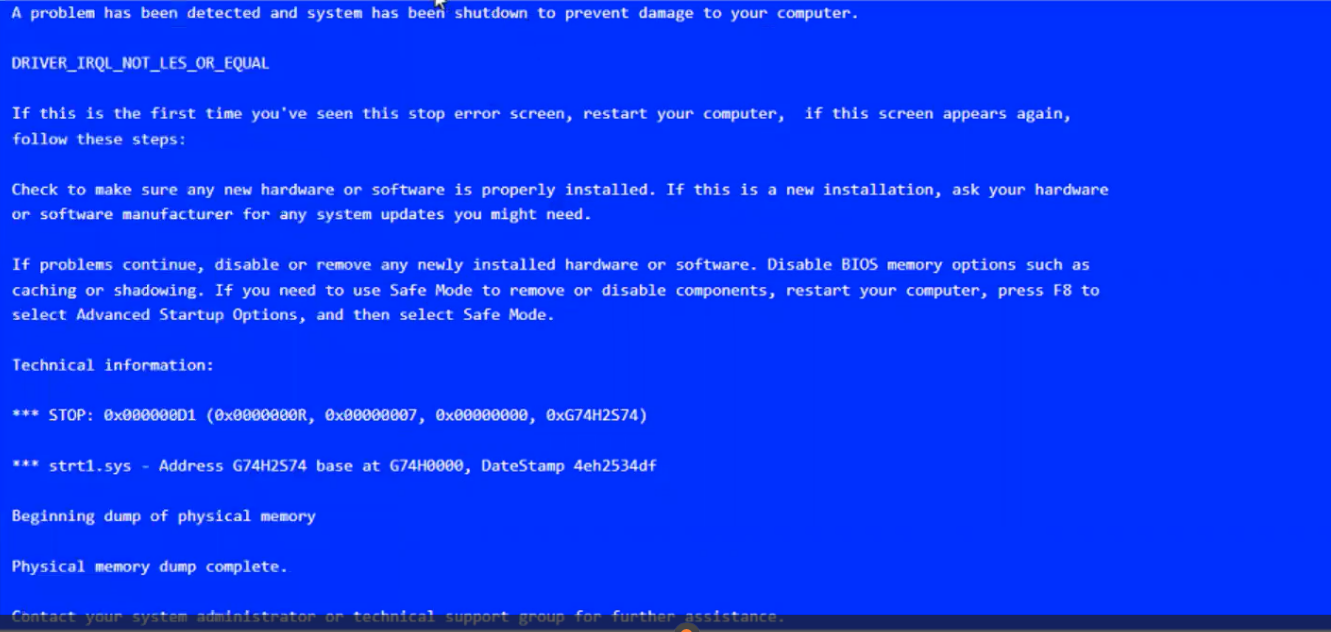
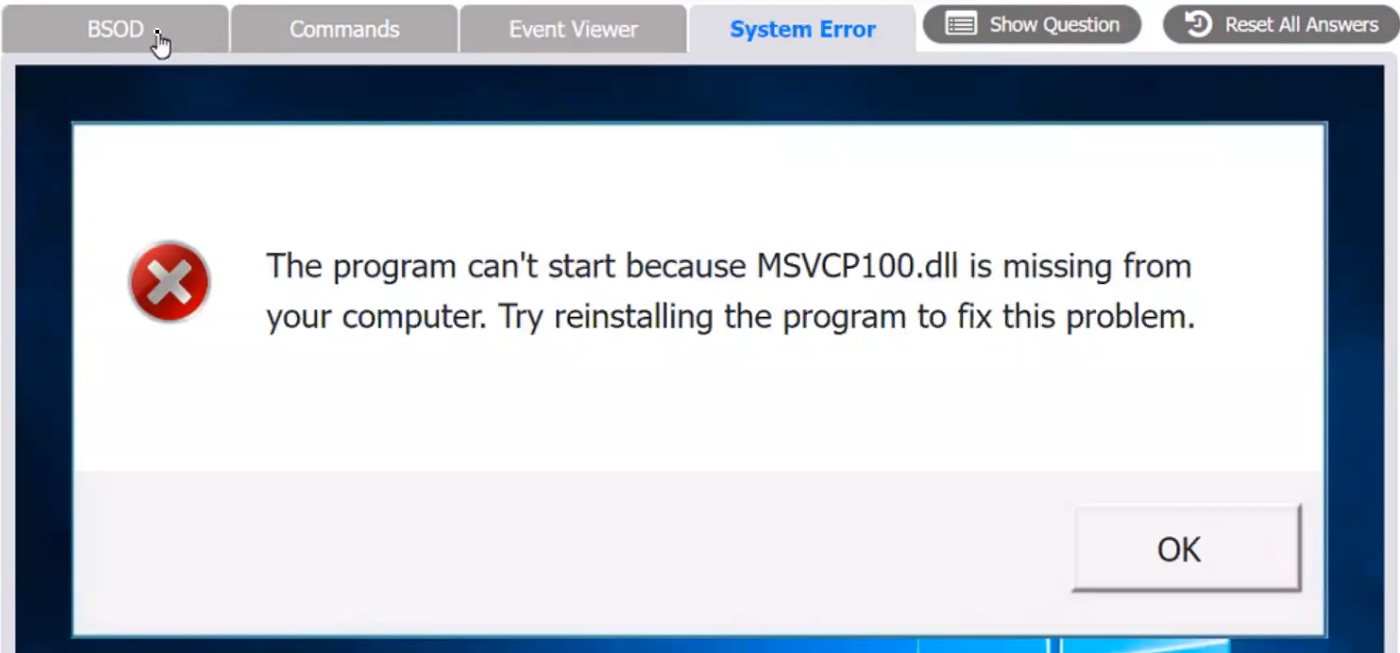
A user reports that after a recent software deployment to upgrade applications, the user can no longer use the Testing program.
However, other employees can successfully use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve any issues discovered by selecting the:
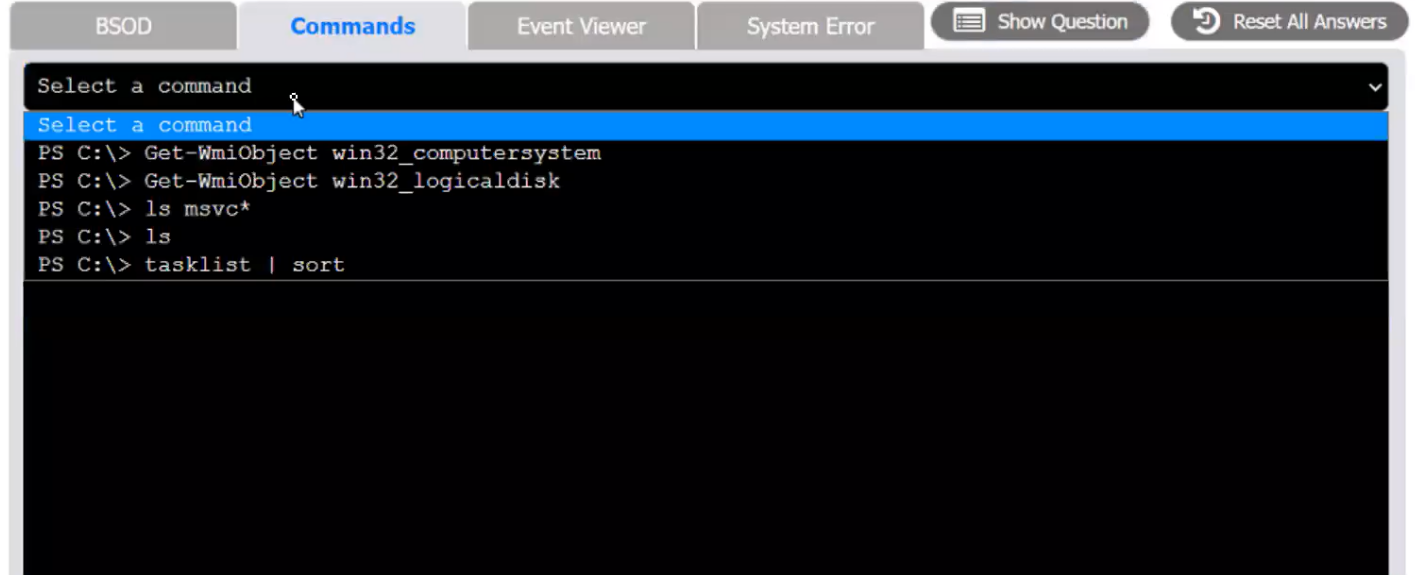
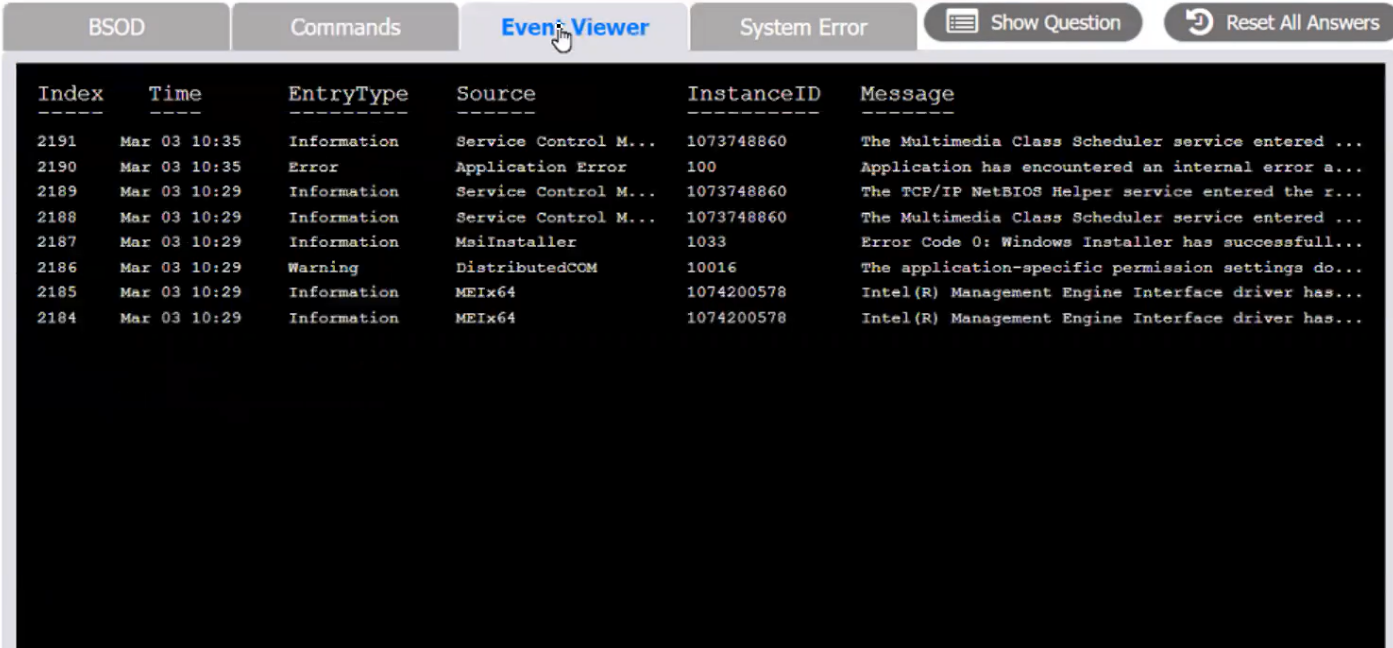
Index number of the Event Viewer issue
First command to resolve the issue
Second command to resolve the issue
BSOD
Commands:
Event Viewer:
System Error:
MultipleChoice
A user is attempting to browse the internet using Internet Explorer. When trying to load a familiar web page, the user is unexpectedly redirected to an unfamiliar website. Which of the following would MOST likely solve the issue? (Choose Correct Answer and provide from Comptia A+ Core2 Study guide or manual from Comptia.org)
Options








