CIW 1D0-571 Exam Questions
- Topic 1: Identify firewall types and define common firewall terminology
- Topic 2: Define encryption and the encryption methods used in internetworking
- Topic 3: Use universal guidelines and principles of effective network security to create effective specific solutions
- Topic 4: Plan a firewall system that incorporates multiple levels of protection, including firewall system design
- Topic 5: Define the significance of network security, and identify various elements of an effective security policy, including risk factors
- Topic 6: Apply security principles and identify security attacks
- Topic 7: security-related organizations, key resources to secure, general security threat types
- Topic 8: proactive detection, setting traps, security breach response, security alerting organizations
Free CIW 1D0-571 Exam Actual Questions
Note: Premium Questions for 1D0-571 were last updated On 03-01-2022 (see below)
Consider the following diagram:
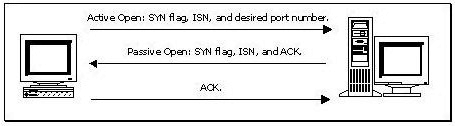
Which of the following best describes the protocol activity shown in the diagram, along with the most likely potential threat that accompanies this protocol?
Which of the following is the most likely first step to enable a server to recover from a denial-of-service attack in which all hard disk data is lost?
You purchased a network scanner six months ago. In spite of regularly conducting scans using this software, you have noticed that attackers have been able to compromise your servers over the last month. Which of the following is the most likely explanation for this problem?
What is the primary use of hash (one-way) encryption in networking?
Which of the following will best help you ensure a database server can withstand a recently discovered vulnerability?
- Select Question Types you want
- Set your Desired Pass Percentage
- Allocate Time (Hours : Minutes)
- Create Multiple Practice tests with Limited Questions
- Customer Support
Currently there are no comments in this discussion, be the first to comment!