Arcitura Education Exam S90.20 Topic 1 Question 19 Discussion
Topic #: 1
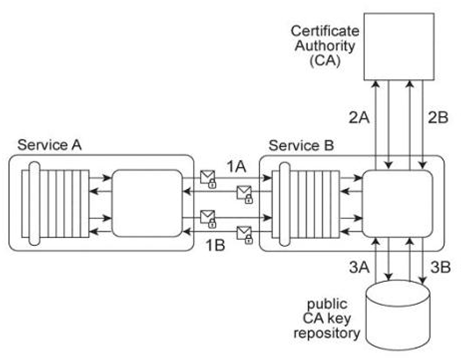
Service A exchanges messages with Service B multiple times during the same runtime service activity. Communication between Services A and B has been secured using transport-layer security. With each service request message sent to Service B (1A .IB), Service A includes an X.509 certificate, signed by an external Certificate Authority (CA). Service B validates the certificate by retrieving the public key of the CA (2A .2B) and verifying the digital signature of the X.509 certificate. Service B then performs a certificate revocation check against a separate external CA repository (3A, 3B). No intermediary service agents reside between Service A and Service B .Service B has recently suffered from poor runtime performance plus it has been the victim of an access-oriented attack. As a result, its security architecture must be changed to fulfill the following new requirements:
1. The performance of security-related processing carried out by Service B when communicating with Service A must be improved.
2. All request messages sent from Service A to Service B must be screened to ensure that they do not contain malicious content. Which of the following statements describes a solution that fulfills these requirements?
Currently there are no comments in this discussion, be the first to comment!