Arcitura Education Exam C90.03 Topic 6 Question 1 Discussion
Topic #: 6
Cloud Provider X (which owns Cloud X) deploys two physical servers (Physical Servers A and B) and two databases (Databases A and B). Virtual Servers A and B are hosted by Physical Server A and Ready-Made Environments A and B are hosted by Virtual Server B . Virtual Servers C and D are hosted by Physical Server B . Cloud Service Consumer A regularly accesses Virtual Server D in order to test and deploy a new cloud service that was developed on-premise by the cloud consumer organization operating Cloud Service Consumer A . Cloud Service Consumer B (operated by a different cloud consumer organization) has been regularly accessing Ready-Made Environment A in order to develop and deploy a different new cloud service. The cloud consumer organizations that own and operate Cloud Service Consumers A and B will soon be ready to launch their respective cloud services for use by their customers. Both cloud consumer organizations are concerned that Cloud X does not provide sufficient security and they demand that Cloud Provider X take the necessary steps to mitigate the denial of service, insufficient authorization and overlapping trust boundaries security threats.
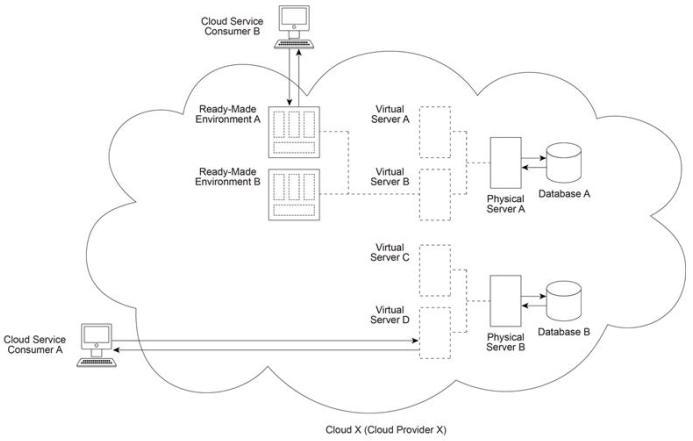
Which of the following statements accurately describes the cloud delivery models used now by the cloud service consumers and in the future by their customers - and - further describes a solution that fulfills the identified security requirements by implementing a single cloud security mechanism?
Delsie
9 days agoSanda
17 days ago