Deal of The Day! Hurry Up, Grab the Special Discount - Save 25% - Ends In 00:00:00 Coupon code: SAVE25
Android Exam AND-802 Topic 3 Question 8 Discussion
Actual exam question for
Android's
AND-802 exam
Question #: 8
Topic #: 3
[All AND-802 Questions]
Topic #: 3
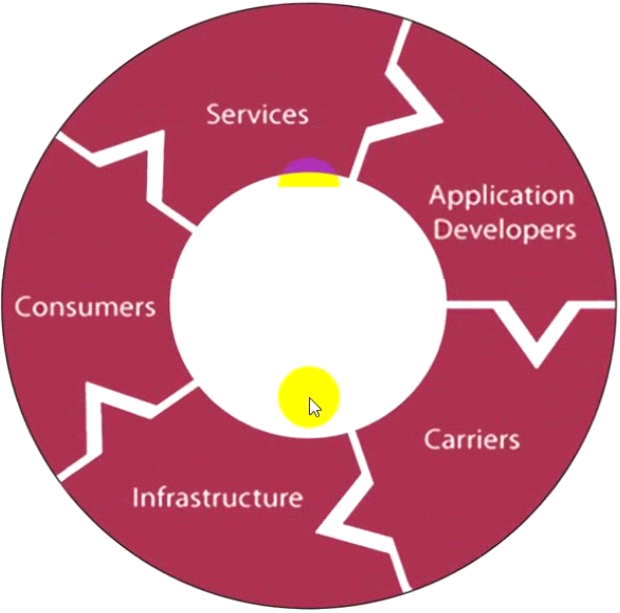
The following image includes some components which you must be aware of to learn about the complexity of the security issue and the fact that software developers can only deal with security issues within their own applications. These components belong to ......................
Suggested Answer:
A
Currently there are no comments in this discussion, be the first to comment!